Table of Contents
Hello guys! I played picoCTF 2023 competition ("picoCTF 2023" or the "Competition") organized by Carnegie Mellon University ("CMU"). I scored 3000+ points in this CTF. These are the challenges i solved during the CTF.
General Skills
- chrono
- money-ware
- permissions
- repitiotions
- useless
- special
- specialer
Forensics
- hideme
- PcapPoisoning
- who is it
- FindAndOpen
- MSB
Reverse Engineering
- Ready Gladiator 0
- Reverse
- Safe Opener 2
- timer
Web Exploitation
- FindMe
- MatchTheRegex
- SOAP
- More SQLi
Cryptography
- HideToSee
- ReadMyCert
- Rotation
- SRA
Binary Exploitation
- two-sum
- VNE
Most of these are basic challenges, so I would like to explain few challenges which are interested me.
Special
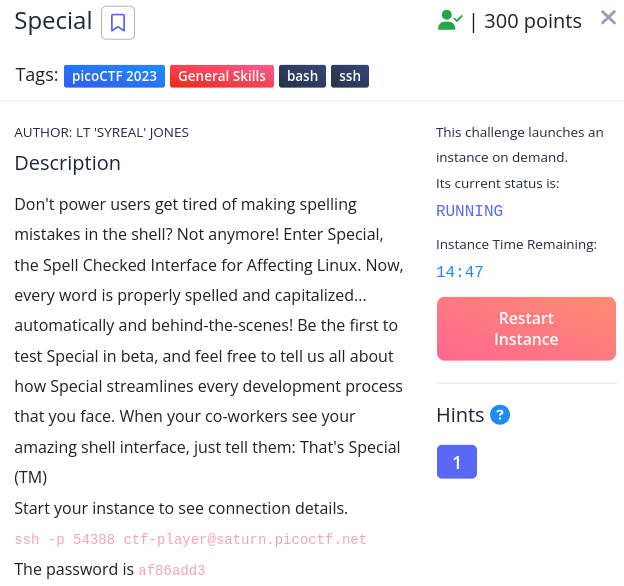
As suggested i used ssh to login to the special machine. And i tried some commands there but those are spell checked by the machine and it results an error to execute the commands. I tries piping technique together with cat command to find the flag location and print out.
Special$ ls
Is
sh: 1: Is: not found
Special$ cat *
Cat *
sh: 1: Cat: not found
Special$ cat | cat *
Cat | cat *
sh: 1: Cat: not found
cat: blargh: Is a directory
Special$ cat | cat blargh/*
Cat | cat blargh/*
sh: 1: Cat: not found
picoCTF{5p311ch3ck_15_7h3_w0r57_6a2763f6}
Flag : picoCTF{5p311ch3ck_15_7h3_w0r57_6a2763f6}
Specialer
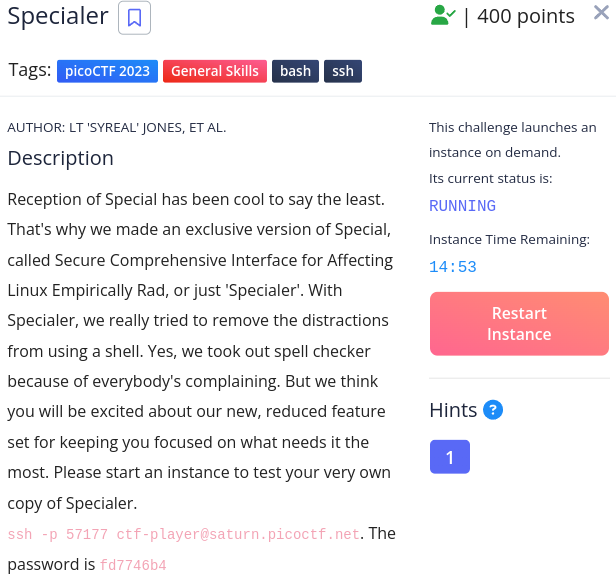
It is similar to the special challenge. Logged into challenge machine and tried few commands to execute.
ctf-player@saturn.picoctf.net's password:
Specialer$ ls
-bash: ls: command not found
Specialer$ echo *
abra ala sim
Specialer$ echo abra/*
abra/cadabra.txt abra/cadaniel.txt
Specialer$ echo ala/*
ala/kazam.txt ala/mode.txt
Specialer$ echo sim/*
sim/city.txt sim/salabim.txt
Specialer$
Using echo I discovered the files present in the machine. Tried to read abra/cadabra.txt with echo. It is not the flag, and the flag is present in the ala/kazam.txt.
Specialer$ echo "$(<abra/cadabra.txt)"
Nothing up my sleeve!
Specialer$ echo "$(<ala/kazam.txt)"
return 0 picoCTF{y0u_d0n7_4ppr3c1473_wh47_w3r3_d01ng_h3r3_38f5cc78}
Specialer$
Flag : picoCTF{y0u_d0n7_4ppr3c1473_wh47_w3r3_d01ng_h3r3_38f5cc78}
two-sum
The source code of the challenge:
#include <stdio.h>
#include <stdlib.h>
static int addIntOvf(int result, int a, int b) {
result = a + b;
if(a > 0 && b > 0 && result < 0)
return -1;
if(a < 0 && b < 0 && result > 0)
return -1;
return 0;
}
int main() {
int num1, num2, sum;
FILE *flag;
char c;
printf("n1 > n1 + n2 OR n2 > n1 + n2 \n");
fflush(stdout);
printf("What two positive numbers can make this possible: \n");
fflush(stdout);
if (scanf("%d", &num1) && scanf("%d", &num2)) {
printf("You entered %d and %d\n", num1, num2);
fflush(stdout);
sum = num1 + num2;
if (addIntOvf(sum, num1, num2) == 0) {
printf("No overflow\n");
fflush(stdout);
exit(0);
} else if (addIntOvf(sum, num1, num2) == -1) {
printf("You have an integer overflow\n");
fflush(stdout);
}
if (num1 > 0 || num2 > 0) {
flag = fopen("flag.txt","r");
if(flag == NULL){
printf("flag not found: please run this on the server\n");
fflush(stdout);
exit(0);
}
char buf[60];
fgets(buf, 59, flag);
printf("YOUR FLAG IS: %s\n", buf);
fflush(stdout);
exit(0);
}
}
return 0;
}
We have to input n1 and n2 those satisfies n1 > n1 + n2 OR n2 > n1 + n2. Mathematically this is not possible. But in computer memory its possible.
This can be done with simple integer overflow.
The n1 and n2 are declared as signed integers.
Signed int range for
2 bytes(-32,768 to 32,767) 4 bytes(-2,147,483,648 to 2,147,483,647)
If we store 2,147,483,648 in a signed 4 byte integer it will become -2,147,483,648.
Take n1 = 2,147,483,648 n2 = 2,147,483,649
Here n1 becomes -2,147,483,648 n2 becomes -2,147,483,647
Therefore, n1 + n2 = -2,147,483,648 + (-2,147,483,647)
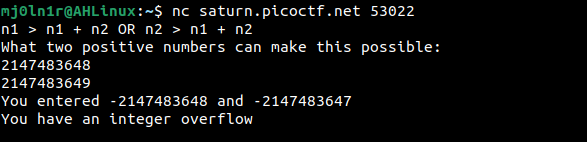
But here, n1>0 and n2>0 not satisfied. We only get the flag if it does.
So, we can select two numbers whose sum is 2147483648. Then the result will be -2147483648.
Take n1 = 2147483640 and n2 = 8
Then n1 + n2 = 2147483648 , it will be stored as -2147483648
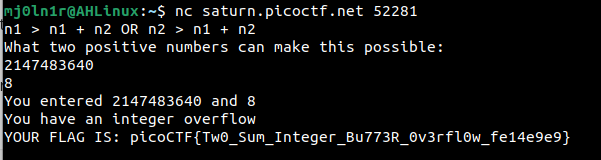
Flag : picoCTF{Tw0_Sum_Integer_Bu773R_0v3rfl0w_fe14e9e9}
For all the solved challenges click here