Table of Contents
- Crypto
- You step away for just ONE minute! 🩸
- Birds!
- Choo Choo!
- Chuck's Code
- Thermodynamic Analysis
- Table for you
- FWN
- Reapeter? Never heard of 'er!
- These Names
- Subject:UMBC['Urgent']
- Crags Hardware Challenge
- Misc
- A Normal Binary Tree
- Ring Ring
- PWN
- Strings Things
- Hello World?
- Rev
- DM Bot!
- DM Bot?
- Binary Bomb Phase 1
- Binary Bomb Phase 2
- Binary Bomb Phase 3
Hello Matesssss! I played DawgCTF 2023 which was happened from 21 Apr to 23 Apr. I played it with the team Invaders0x1.
This time its a BANGG... Yes, we ranked Top 6 globally. Yes, we Invaders0x1 got 6th in DawgCTF2023. I got one first blood 🩸 and we are in the top solvers list in many challenges.
Crypto
You step away for just ONE minute! 🩸
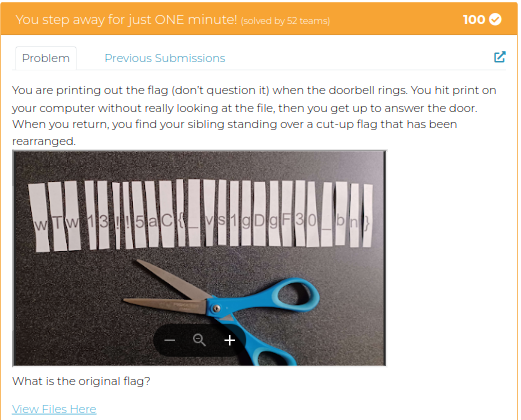
Cipher text : wTw13!!5aC{_vs1gDgF30_bn}
I know this is a transposition cipher. Immediately I used this site and bruteforced the cipher to get the flag.
I saw someone(smart) used this program to solve.
scramble = "wTw13!!5aC{_vs1gDgF30_bn}"
idx= scramble.index('D')
flag = ""
for i in range(len(scramble)):
flag += scramble[idx]
idx = (idx - 8)% len(scramble)
print(flag)
Flag : DawgCTF{w3_10v3_s!b1!ng5}
Birds!
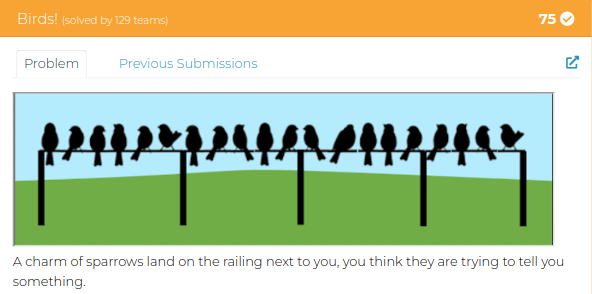
And a quick search on google results bird on the wire cipher
Solved the chall using this site
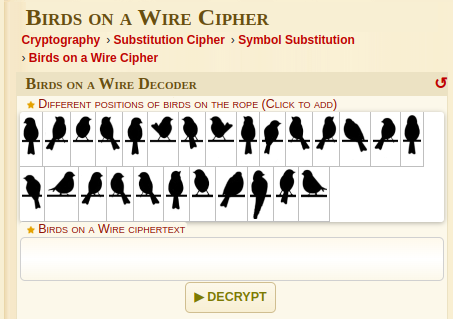
Plain text : ONEINHANDORTWOINBUSH
Flag : ONEINHANDORTWOINBUSH
Choo Choo!
Cipher text : D1_a4nrCwrs30gt_poC_tu1T3h5!Fk3_}{1y31l_r_4
They are talking about rail and i know its reil fence cipher. And they are hinted that 10, so I used 10 as the key for reilfence cipher.
Using this site will be helpful.
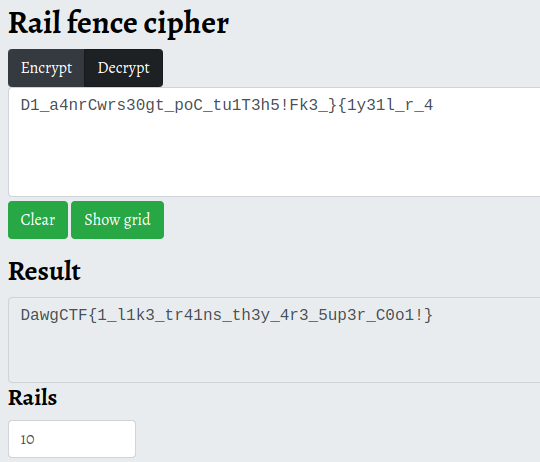
Flag : DawgCTF{1_l1k3_tr41ns_th3y_4r3_5up3r_C0o1!}
Chuck's Code
The attached file contains these 0's
0 0 00 000 0 0 00 00 0 00 00 0000 0 0000 00 0 0 00000 00 00 0 0000 00 0000 0 000 00 0 0 0 00 0 0 0 00 00 0 0 00 000 0 00 00 0 0 0000 00 0 0 0000 00 000 0 0000 00 0 0 0 00 000 0 000 00 0 0 0 00 0 0 000 00 000 0 0000 00 0 0 0 00 0 0 000 00 0 0 0000000 00 0 0 000 00 00 0 00 00 0000 0 000 00 00 0 0 00 0 0 000 00 00 0 0 00 00 0 00 00 000 0 0000 00 00 0 000 00 0 0 00000000 00 00000 0 00 00 0000 0 000 00 0 0 000 00 0 0 00 00 00 0 00000 00 00 0 0 00 0 0 000 00 00 0 00 00 0 0 0 00 0000 0 000000 00 0 0 0
Searched on google for chucks cipher to confirm wheather it is existed or not. Found that it is existed! Used this site and selected 7-bit ASCII encoding. And decrypted the flag.
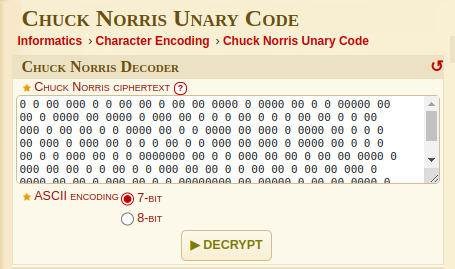
Flag: DawgCTF{chuck_n0rr1s_p0w3rs!}
Thermodynamic Analysis
The attached file contains these physics formales.
D=1/2mv^2 (force * displacement) = 1/2 * mass * velocity^2 + alpha
w=fd (force * displacement) with respect to displacement lag
Cp=20.79 J/K/Mol for a constant pressure ONLY FOR OUTPUT
FINAL TEMPERATURE ALWAYS COMES FIRST BECAUSE THE TEMPERATURE DELTA IS INSIDE {
temperature min, temperature max}, like with
e=u+pVr
m=0
dU=mcdT and remember that sometimes mcdT can be a dy
nA is number of moles of gas A/B^4
mA*cA*∆T=cB*cB*∆T when two things are equalizing i.e and indirect carnot cycli
c, such as with the following equation: 2500kg*cA*(500-400)=cB*cB*∆T*5
s=ksubb * ln * omega * tau
cv=12.47J/K/Mol for a constant vol, Klevin is k
s=integral from vi to vf of (1/T *dU) for a general delta!
}]\d\wa\dT
h=W/ti (Power) = Work / time elapsed in seconds i
sv=dx/dm, aka momentum i
singleton particles are usually carrying a charged ion
0*pe=mgh aka potential energy with respect to gravity zeroed to t
p=x^8/fd+a
radial work=fd force * displacement
overall pv=nrt (pressure * volume) = (quantity of gas) * (avagadro's num) * temp f
the equilibrium pos of a container filled with ideal gas h
extended to a near symmetrical distribution of constant mass f
less than with uniform distribution=(nA/(na+nB))*L where L=na
g+nA is number of moles of gas A/B!
Total num of states = (Volf/Voli)^n
mA*cA*∆T=cB*cB*∆T when two things are equalizing via direct conduction
Qa=Qb (heat lost equals heat gained, because of conservation of energy,
use this to solve for etc)
∆T=(Tf-Ti) (when temperature is decreasing, this becomes (Ti - Tf))
When we have a material that changes states, i.e ice to water,
our equation should look something like this:
Q=m*cA*(Tm-Ti) + m*cB*(T-Tm) + m*L (where cA is the specific heat of the initi
al state, cB is the specific heat of the state it transforms into, and
L is the latent heat of fusion for that state change, and Tm is the temp
at which the state change occurs)
REMEMBER - YOU CAN SET FUNCTIONS EQUAL TO ANOTHER AND CANCEL LIKE TERMS
(for instance, if kinetic energy is converted completely to heat, you can
set K=mC∆T and solve even without knowing m)
REMEMBER - When a material is initially at it's state change point, and
then is equalized or heated, you ignore
U = f/2nRT where R is the gas constant and f is the degrees of freedom
p is pascals, v is volume in m, n is moles, R is 8.314, T is kelvin temp
∆S = Change in entropy
∆U = n Cp ∆T where U is internal energy of an ideal gas
KE=3/2nRT
Avg Kinetic Energy per Molecule
KE=3/2KbT
Average velocity of atoms in an ideal gas
V = sqrt(3RT/m) (Where R is 8.314, and m is atomic mass * Avagadro)
∆L=L0α(∆T)
∆Q = m * Csteel * (∆T)
W=P*∆V
Cv=12.47J/K/Mol for a constant vol
Cp=20.79 J/K/Mol for a constant pressure
avagadro's number - 8.314
In general, ∆S=integral from vi to vf of (1/T *dU)
for constant temp, this is ∆S = ∆U/T
for changing temp, this is ∆S = m*c*ln(Tf/Ti)
USE KELVIN FOR ENTROPY
∆U=Q=mc∆T
dU=mcdT
Lice*Mice+MiWater*CiWater*(T-273.15)=Mwater*Cwater*(363.15-T)
100*333500+100*4200*(T-273.15)=500*4200*(363.15-T)
Eice=33350000/273=122000
Eiwater=100*4200*ln(334.9/273.15)=85600.5716825
Ewater=500*4200*ln(334.9/363.15)=-510199.151188
T=334.915873016
When I closesly observed the text, I found that the first line starts with D and ends with a , Seconds line starts with w ends with g. It is the flag format nd thats the solution, I wrote this simple
solve.py to print the flag.
with open("STUDYME.txt","r") as f:
l = f.readlines()
# print(l)
for i in l:
i = i.strip()
print(i[0]+i[-1],end="")
# DawgCTF{therm0dyn4mic5sucks!}
Flag: DawgCTF{therm0dyn4mic5sucks!}
Table for you
Attached file : ahahahwhatsthemagicword(notgoodbytes).zip
I didnt solved it during CTF. I was 10 min late to solve it :(
The zip file given is password encrypted, I tried to crack it using john its not worked. Then i searched for ahahah whats the magic word on google, found that it was a dialogue from Jurassic Park movie. After reading few articles, I found that the magic word is please.
With please as password the zip is extracted ahahahwhatsthemagicword.db. Opened it using sqlite online viewer.
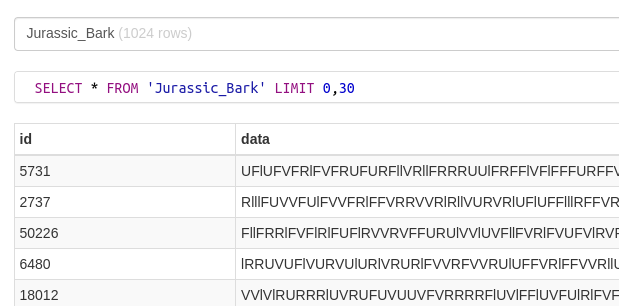
The database had a table with garbage values. Actually all are not garbage, one row has the flag. I used online cipher identifier to identify the cipher type. The result is base62 so i bruteforced all the 1024 lines of data with base62 decode. And the CTF was ended -_-
Later I got to know about it was bas64 and the == was removed by the challenge auther. ^_^
I found that the row with id 64545 has the base64 encoded strings
RUVFRUVFRUVFZUVFRWVFRUVFRUVFRUVFRWVlRUVFRWVFRUVFRUVFRUVlZWVFZWVlRUVFRUVFRUVFZWVFRWVlZUVFRUVFRUVFRWVFRUVFZWVFRUVFRUVFRUVlRWVFZUVFRUVFRUVFRUVFZUVFRWVlRUVFRUVFRUVFRWVlZWVFZWVFRUVFRUVFRUVlZWVlRUVlRUVFRUVFRUVFRWVlRUVFRUVFRUVFRUVFRWVlZUVlRWVFRUVFRUVFRUVlRWVlZWVlRUVFRUVFRUVFZWVFZUVlZUVFRUVFRUVFRWVlRWVlZUVFRUVFRUVFRUVFZWVFRWVlRUVFRUVFRUVFZWVlRWVlZUVFRUVFRUVFRWVFZWVlZWVFRUVFRUVFRUVlZWVFZUVFRUVFRUVFRUVFZWVFZUVFRUVFRUVFRUVFRUVlZUVFZWVFRUVFRUVFRUVlRWVlZWVlRUVFRUVFRUVFZWVFZWVFZUVFRUVFRUVFRUVlZUVlRUVFRUVFRUVFRUVlZUVFZWVlRUVFRUVFRUVFRWVlRUVFZUVFRUVFRUVFRWVlRUVFZWVFRUVFRUVFRUVlRWVlZWVlRUVFRUVFRUVFZWVlRWVlZUVFRUVFRUVFRUVlZUVFRUVFRUVFRUVFRUVlZWVFRWVFRUVFRUVFRUVFZWVFRWVFRUVFRUVFRUVFRUVlRUVFRWVFRUVFRUVFRUVlZWVlZUVl
Added == at the end and decoded it from base64.
EEEEEEEEEeEEEeEEEEEEEEEEEeeEEEEeEEEEEEEEEeeeEeeeEEEEEEEEEeeEEeeeEEEEEEEEEeEEEEeeEEEEEEEEEeEeEeEEEEEEEEEEEeEEEeeEEEEEEEEEEeeeeEeeEEEEEEEEEeeeeEEeEEEEEEEEEEeeEEEEEEEEEEEEEeeeEeEeEEEEEEEEEeEeeeeeEEEEEEEEEeeEeEeeEEEEEEEEEeeEeeeEEEEEEEEEEEeeEEeeEEEEEEEEEeeeEeeeEEEEEEEEEeEeeeeeEEEEEEEEEeeeEeEEEEEEEEEEEeeEeEEEEEEEEEEEEEeeEEeeEEEEEEEEEeEeeeeeEEEEEEEEEeeEeeEeEEEEEEEEEEeeEeEEEEEEEEEEEeeEEeeeEEEEEEEEEEeeEEEeEEEEEEEEEeeEEEeeEEEEEEEEEeEeeeeeEEEEEEEEEeeeEeeeEEEEEEEEEEeeEEEEEEEEEEEEEeeeEEeEEEEEEEEEEeeEEeEEEEEEEEEEEEeEEEEeEEEEEEEEEeeeeeEe
Marked E = 0 and e = 1 Then converted binary to ascii and got the flag.
000000000100010000000000011000010000000001110111000000000110011100000000010000110000000001010100000000000100011000000000011110110000000001111001000000000011000000000000011101010000000001011111000000000110101100000000011011100000000000110011000000000111011100000000010111110000000001110100000000000110100000000000001100110000000001011111000000000110110100000000001101000000000001100111000000000011000100000000011000110000000001011111000000000111011100000000001100000000000001110010000000000110010000000000001000010000000001111101
Converting this binary string to ASCII will give us the flag.
FWN
Lets get into ForensicsWebNetwork Challenges. We solved all the challenges from FWN category, these are the challenges i solved in CTF.
Reapeter? Never heard of 'er!
Searched for MD repeater database on google and found this site.
As the challenge description says that we have to find the closest maryland MD repeater to Green Ridge Forest on 6m channel.
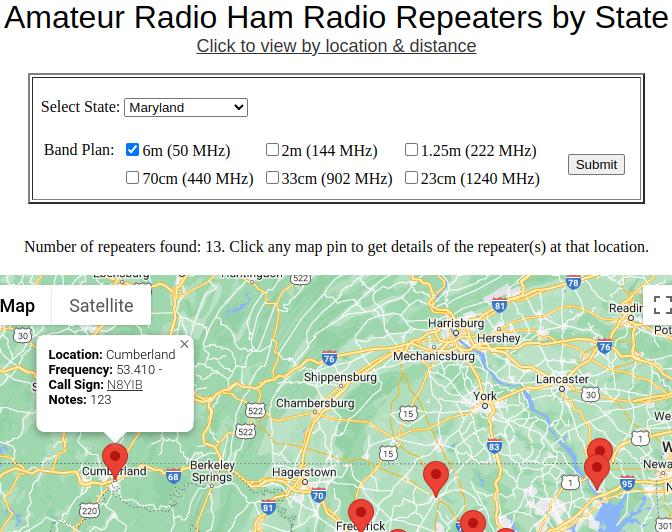
As we can see the repeater located in Cumberland has the closest distance from Green Ridge Forest. And the flag is the call sign of this tower i.e, N8YIB
Flag : DawgCTF{N8YIB}
These Names
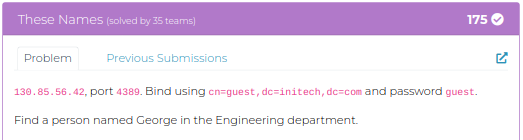
Again I had no clue on this challenge, searched these options on google. I got to know that they are talking about ldap connection. After searching a while I found a way to connect ldap server using these creds.
Connetion to ldap server.
mj0ln1r@Linux:~/thesenames$ ldapsearch -x -D "cn=guest,dc=initech,dc=com" -W -H ldap://130.85.56.42:4389 -b "cn=guest,dc=initech,dc=com" >> guest_result.txt
This will save the output of the ladap server in guest_result.txt.
Sample data in guest_result.txt
# extended LDIF
#
# LDAPv3
# base <cn=guest,dc=initech,dc=com> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# guest, , initech.com
dn: cn=guest,ou=,dc=initech,dc=com
cn: guest
uid: guest
ou:
uidNumber: 0
accountStatus: active
objectClass: posixAccount
objectClass: shadowAccount
loginShell: /bin/bash
homeDirectory: /home/guest
description: guest
gecos: guest
gidNumber: 0
shadowExpire: -1
shadowFlag: 134538308
shadowInactive: -1
shadowLastChange: 11000
shadowMax: 99999
shadowMin: -1
shadowWarning: 7
# blumbergh, executives, initech.com
dn: cn=blumbergh,ou=executives,dc=initech,dc=com
cn: blumbergh
uid: blumbergh
givenName: Bill
ou: executives
uidNumber: 0
accountStatus: active
objectClass: posixAccount
objectClass: shadowAccount
loginShell: /bin/bash
homeDirectory: /home/blumbergh
description: blumbergh
gecos: blumbergh
gidNumber: 100
memberOf: ou=executives,ou=groups,dc=initech,dc=com
shadowExpire: -1
shadowFlag: 134538308
shadowInactive: -1
shadowLastChange: 11000
shadowMax: 99999
shadowMin: -1
shadowWarning: 7
There are thounsands of similar entries are available in guest_result.txt. The challenge said that I have to find George from Engineering department.
# gdingley, engineering, initech.com
dn: cn=gdingley,ou=engineering,dc=initech,dc=com
cn: gdingley
uid: gdingley
givenName: George
ou: engineering
uidNumber: 0
accountStatus: active
objectClass: posixAccount
objectClass: shadowAccount
loginShell: /bin/bash
homeDirectory: /home/gdingley
description: gdingley
gecos: gdingley
gidNumber: 400
memberOf: ou=engineering,ou=groups,dc=initech,dc=com
shadowExpire: -1
shadowFlag: 134538308
shadowInactive: -1
shadowLastChange: 11000
shadowMax: 99999
shadowMin: -1
shadowWarning: 7
secretemployeeinformation: RGF3Z0NURntpX2FpbnRfbm9fbGlnaHR3ZWlnaHR9
The secretemployeeinformation looks like a base64 encode. Decoded it and I got the flag.
mj0ln1r@Linux:~/thesenames$ echo "RGF3Z0NURntpX2FpbnRfbm9fbGlnaHR3ZWlnaHR9" base64 -d
DawgCTF{i_aint_no_lightweight}
Flag : DawgCTF{i_aint_no_lightweight}
Subject:UMBC['Urgent']
Attached file: UMBC.jpg
Checked the hex of image, at the end of image binary bits are present.
mj0ln1r@Linux:~/UMBC$ xxd UMBC.jpg | tail
000a6960: d29e f5d5 14ab 2b41 ebd9 ff00 999f 2d9d ......+A......-.
000a6970: cbf6 0d25 bcc0 2dc4 8d18 fba8 e725 3fdd ...%..-......%?.
000a6980: 6eb8 f639 ab1a ae87 06a7 134a c064 1e66 n..9.......J.d.f
000a6990: 45fb a7fd a5ed f515 7a7b 0b2d 6fc3 a7c4 E.......z{.-o...
000a69a0: 7a64 4d66 b19d b2db 31ca 839e aa7d 3eb5 zdMf....1....}>.
000a69b0: 474c 96f2 16f3 9665 d8c7 e518 e7dc 1f51 GL.....e.......Q
000a69c0: 5cb5 2927 b16a 76d4 0110 0011 0100 0111 \.)'.jv.........
000a69d0: 0100 0110 0111 1010 0110 0011 0011 0001 ................
000a69e0: 0100 1110 0011 0000 0101 1010 0101 0111 ................
000a69f0: 0110 0011 0011 1101 ffd9 ..........
Tried to convert these bits into ASCII, this writeup have a perl line to convert ascii. (A bit interested on using perl)
mj0ln1r@Linux:~/UMBC$ echo 011000110100011101000110011110100110001100110001010011100011000001011010010101110110001100111101 | perl -lpe '$_=pack"B*",$_'
cGFzc1N0ZWc=
mj0ln1r@Linux:~/UMBC$ echo "cGFzc1N0ZWc=" | base64 -d
passSteg
Now I tried steghide if there is any data hidden inside image. And before that removed binary bits from the image with this website. The steghide prompted for password used passSteg for it and it extracted f.txt which contains the flag.
mj0ln1r@Linux:~/UMBC$ steghide extract -sf UMBC_edited.jpg
Enter passphrase: passSteg
wrote extracted data to "f.txt".
mj0ln1r@Linux:~/UMBC$ cat f.txt
DawgCTF{b1n4ry_64_p4ssw0rd}
Flag : DawgCTF{b1n4ry_64_p4ssw0rd}
Crags Hardware Challenge
Attached Files : hardwarechallenge.wav
There is a wav file present in challenge and they are talking about oscilloscope I dont know what is it. Again a quick google search results it is an intrument to analyze audio. So I searched for online oscilloscope viewer found this site oscilloscope.
And used the above site to view wav file in oscilloscope and immediately it resulted me the flag.
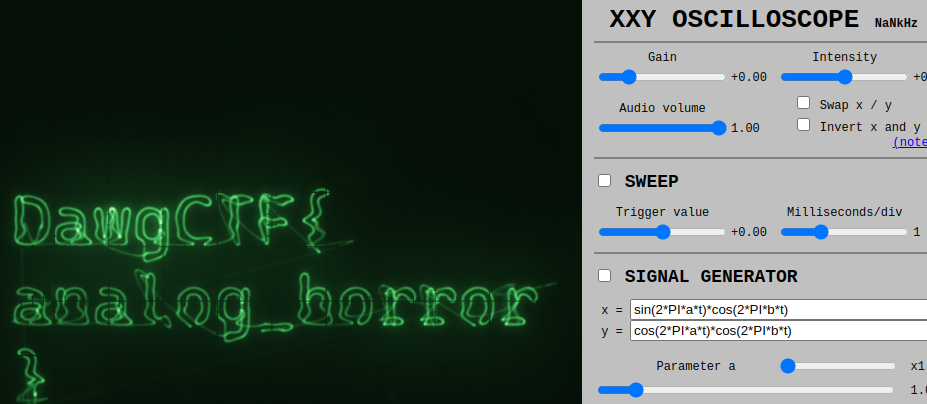
Flag : DawgCTF{analog_horror}
Misc
A Normal Binary Tree
Attached File : problem.txt
So, we need to build a binary tree with these nodes and the post order traversal of this binary tree will be the flag.
I tried many binary tree programs to do this in online, sadly no one works fine. So I went back to geeksforgeeks and learned binary tree from it and constructed the binary tree, traversed it by hand.
I used this tool to simulate the binary tree.
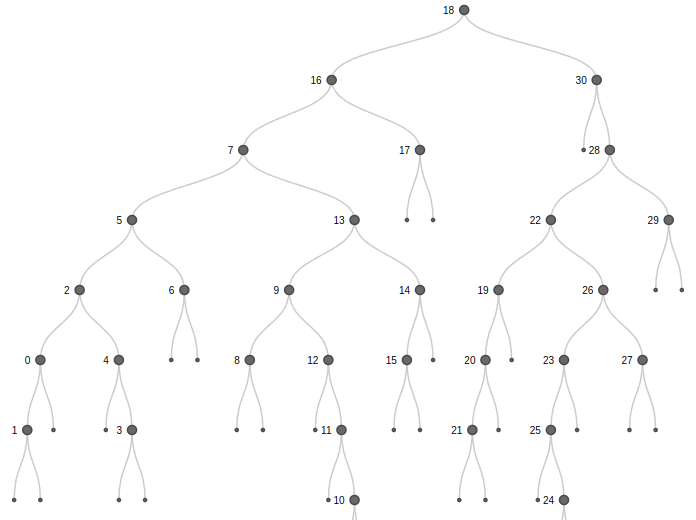
Noted the post order travesal of nodes in a list and printed the corresponding characters of it.
data = [(18, '}'), (30, '!'), (16, '_'), (7, 's'), (28, 't'), (13, '1'), (22, '3'), (9, 't'), (26, 'r'), (5, 'F'), (12, 'n'), (2, 'C'), (23, '0'), (0, 'a'), (11, '0'), (14, 'm'), (4, 'g'), (17, 's'), (25, 'f'), (19, '3'), (1, 'D'), (20, 'h'), (27, 'r'), (3, 'w'), (6, 'T'), (29, 's'), (15, '_'), (24, '_'), (8, '{'), (10, 'D'), (21, 't')]
sorted_data = sorted(data, key=lambda x: x[0])
chars = ''.join([d[1] for d in sorted_data])
ans = [1,0,3,4,2,6,5,8,10,11,12,9,15,14,13,7,17,16,21,20,19,24,25,23,27,26,22,29,28,30,18]
for i in ans:
print(sorted_data[i][1],end="")
#DawgCTF{D0nt_m1ss_th3_f0rr3st!}
Later I wrote this complete automated script which doesn't need paper work by hand.
class Node:
def __init__(self, value):
self.value = value
self.left = None
self.right = None
def insert(node, value, char):
if node is None:
return Node((value, char))
if value < node.value[0]:
node.left = insert(node.left, value, char)
else:
node.right = insert(node.right, value, char)
return node
def postorder_traversal(node):
if node:
postorder_traversal(node.left)
postorder_traversal(node.right)
print(node.value[1], end='')
# Sample input values
values = [(18, '}'), (30, '!'), (16, '_'), (7, 's'), (28, 't'), (13, '1'), (22, '3'), (9, 't'), (26, 'r'),
(5, 'F'), (12, 'n'), (2, 'C'), (23, '0'), (0, 'a'), (11, '0'), (14, 'm'), (4, 'g'), (17, 's'),
(25, 'f'), (19, '3'), (1, 'D'), (20, 'h'), (27, 'r'), (3, 'w'), (6, 'T'), (29, 's'), (15, '_'),
(24, '_'), (8, '{'), (10, 'D'), (21, 't')]
root = None
for value in values:
root = insert(root, value[0], value[1])
postorder_traversal(root) # Output: DawgCTF{D0nt_m1ss_th3_f0rr3st!}
Flag : DawgCTF{D0nt_m1ss_th3_f0rr3st!}
Ring Ring
We have find the state and town of the call made by (227-759-4976)
After surfing the web for a while I found this number on this site.
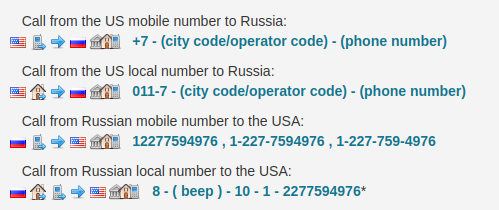
I observed that the call originated from USA Now I used USA country code(+1) to search about phone number.
I got to know about that 227 is area code of the number location. Searched for the State of the area code 227. After visiting many sites, I found this map.
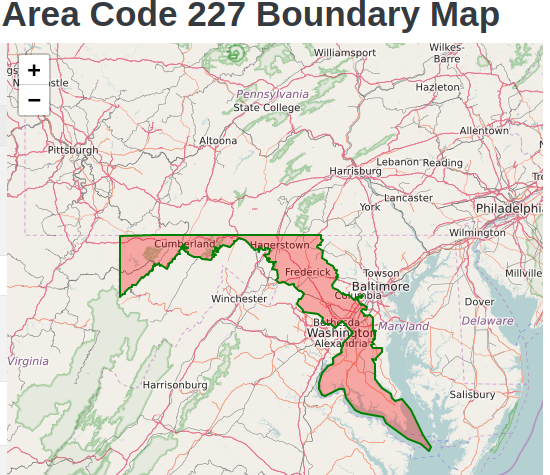
The State is maryland and the Town is Cumberland.
Flag : DawgCTF{cumberland_maryland}
PWN
Strings Things
Attached file : secrets
As the challenge name suggests, the strings done the things.
mj0ln1r@AHLinux:~/strings$ strings secrets
/lib64/ld-linux-x86-64.so.2
gE%*
0?{H
libstdc++.so.6
__gmon_start__
_ITM_deregisterTMCloneTable
_ITM_registerTMCloneTable
libm.so.6
libgcc_s.so.1
libc.so.6
puts
stdin
printf
fgets
strcspn
strcmp
__libc_start_main
GLIBC_2.2.5
=m
<=t9H
struct fH
getsf
[]A\A]A^A_
ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/
RGF3Z0NURntzdHIxbmc1X3cxbmc1fQ
supers3cr3tpassword
Enter the password:
You did it!
The flag is: %s
Incorrect password. Try again.
;*3$"
GCC: (GNU) 8.5.0 20210514 (Red Hat 8.5.0-15)
GCC: (GNU) 8.5.0 20210514 (Red Hat 8.5.0-16)
3p1067
supers3cr3tpassword got my eyes. Normally I started running the binary file and it prompted for password and I used supers3cr3tpassword and it resulted the flag.
mj0ln1r@AHLinux:~/strings$./secrets
Enter the password: supers3cr3tpassword
You did it!
The flag is: DawgCTF{str1ng5_w1ng5}
Flag : DawgCTF{str1ng5_w1ng5}
Hello World?
Attached File : HelloWorld
They said the program workd for any name! I thought that what about if the name is toooo long.
mj0ln1r@AHLinux:~/helloworld$ ./HelloWorld
What is Your Name?
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
DawgCTF{n4m3_0v3rfl0w}
The thought --> flag
Flag : DawgCTF{n4m3_0v3rfl0w}
Rev
DM Bot!
Attached File : unclaimed_bot.py
The unclaimed_bot.py
import discord
if __name__ == "__main__":
client = discord.Client(intents=discord.Intents.default())
@client.event
async def on_ready():
print('We have logged in as {0.user}'.format(client))
klist = ["TG9yZW0gaXBzdW0gZG9sb3Igc2l0IGFtZXQsIGNvbnNlY3RldHVyIGFkaX","Bpc2NpbmcgZWxpdCwgc2VkIGRvIGVpdXNtb2QgdGVtcG9yIGluY2lkaWR1bnQgdXQgbGFib3JlIGV0IGRvbG9yZSBtYWduYSBhbGlxdWEuIFVybmEgY29uZGltZW50dW0gbWF0dGlzIHBlbGxlbnRlc3F1ZSBpZCBuaWJoIHRvcnRvciBpZCBhbGlxdWV0LiBGYW==","NpbGlzaXMgbWFnbmEgZXRpYW0gdGVtcG9yIG9yY2kgZXUH607JkNwW8rNqyEwI0KsHSXavqGb3iXl0PnPvpa72f8=uIFNhcGllbiBldCBsaWd1bGEgdWxsYW1jb3JwZXIgbWFsZXN1YWRhLiBUcmlzdGlxdWUgbnVsbGE","gYWxpcXVldCBlbmltIHRvcnRvciBhdC4gUXVpcyByaXN1cb'kpXpSMY0j53jg-b-WFChVOmcn5r20RktR66SB3_BYwE='yBzZWQgdnVscHV0YXRlIG9kaW8uIFNhZ2l0dGlzIGFsaXF1YW0gbWFsZXN1YWRhIGJpYmVuZHVt","IGFyY3Ugdml0YWUgZWxlbWRGF3Z0NURns1dDR0MWNfMHJfZHluNG0xYz99VudHVtIGN1cmFiaXR1ci4gSGFiaXRhc3NlIHBsYXRlYSBkaWN0dW1zdCBxdW=","lzcXVlIHNhZ2l0dGlzIHB1cnVzIHNpdCBhbWV0LiBQdXJ1cyBncmF2aWRhIHF1aXMgYmxhbmRpdCB0dXJwaXMgY3Vyc3VzIGluIGhhYyBoYWJpdGFzc2UuIFZvbHV0cGF0IGFjIHRpbmNpZHVudCB2aXRhZSBzZW1wZXIuIFF1YW0gZWxlbWVudHVtIHB1b==","HZpbmFyIGV0aWFtIG5vbiBxdWFtIGxhY3VzLiBBbWV0IHRlbGx1cyBjcmFzIGFkaXBpc2NpbmcgZW5pbSBldSB0dXJwaXMgZWdlc3Rhcy4KCkZldWdpYXQgbmlzbCBwcmV0aXVtIGZ1c2NlIGlkIHZlbGl0IHV0IHRvcnRvciBwcmV0aXVtIHZpdmVycmEuIEVuaW0gZGlhbSB2dWxwdXRhdGUgdXQgcGhhcmV0cmEgc2l0IGFtZ","XQuIEZldWdpYXQgcHJldGl1bSBuaWJoIGlwc3VtIGNvbnNlcXVhdCBuaXNsLiBCaWJlbmR1bSB1dCB0cmlzdGlxdWUgZXQgZWdlc3RhcyBxdWlzIGlwc3VtIHN1c3BlbmRpc3NlIHVsdHJpY2VzLiBWaXZlcnJhIGlwc3VtIG51bmMgYWxpcXVldCBi","aWJlbmR1bSBlbmltIGZhY2lsaXNpcyBncmF2aWRhIG5lcXVlLiBDb25zZWN0ZXR1ciBhZGlwaXNjaW5nIGVsaXQgdXQgYWxpcXVhbSBwdXJ1cyBzaXQgYW1ldCBsdWN0dXMuIEVyYXQgdmVsaXQgc2NlbG","VyaXNxdWUgaW4gZGljdHVtIG5vbiBjb25zZWN0ZXR1ciBhIGVyYXQuIERpYW0gc29sbGljaXR1ZGluIHRlbXBvciBpZCBldSBuaXNsIG51bmMgbWkgaXBzdW0uIFJpc3VzIHF1aXMgdmFyaXVzIHF1YW0gcXVpc3F1ZSBpZCBkaWFtIHZlbCBxdWFtIGV","sZW1lbnR1bS4gUG9zdWVyZSBsb3JlbSBpcHN1bSBkb2xvciBzaXQgYW1ldCBjb25zZWN0ZXR1ci4gVWxsYW1jb3JwZXIgbW9yYmkgdGluY2lkdW50IG9ybmFyZSBtYXNzYS4gUXVhbSBhZGlwaXNjaW5nIHZpdGFlIHByb2luIHNhZ2l0dGlzIG5pc2wgcmhvbmN1cy4gRXUgY29uc2VxdWF0IGFjIGZlbGlzIGRvbmVjIGV0IG9kaW8gcGVsbGVudGVzcX","VlIGRpYW0gdm9sdXRwYXQuIEV0IG1hZ25pcyBkaXMgcGFydHVyaWVudCBtb250ZXMgbmFzY2V0dXIuIEFsaXF1YW0gbWFsZXN1YWRhIGJpYmVuZHVtIGFyY3Ugdml0YWUuIEluIG51bGxhIHBvc3VlcmUgc29sbGljaXR1ZGluIGFsaXF1YW0u"]
mlist = ["TG9yZW0gaXBzdW0gZG9sb3Igc2l0IGFtZXQsIGNvbnNlY3RldHVyIGFkaX","Bpc2NpbmcgZWxpdCwgc2VkIGRvIGVpdXNtb2QgdGVtcG9yIGluY2lkaWR1bnQgdXQgbGFib3JlIGV0IGRvbG9yZSBtYWduYSBhbGlxdWEuIFVybmEgY29uZGltZW50dW0gbWF0dGlzIHBlbGxlbnRlc3F1ZSBpZCBuaWJoIHRvcnRvciBpZCBhbGlxdWV0LiBGYW==","NpbGlzaXMgbWFnbmEgZXRpYW0gdGVtcG9yIG9yY2kgZXUH607Jb'gAAAAABkQfn3TpdZBGFeG4VfZObYKIL3f25CVBupi27swEARiUnK6c6ry6951JgI9lPqbPa3MkJ0Yg5huinb6_SNoTVZp1wdvYiIo3QZd-qb1p-nDsOeX_I='kNwW8rNqyEwI0KsHSXavqGb3iXl0PnPvpa72f8=uIFNhcGllbiBldCBsaWd1bGEgdWxsYW1jb3JwZXIgbWFsZXN1YWRhLiBUcmlzdGlxdWUgbnVsbGE","gYWxpcXVldCBlbmltIHRvcnRvciBhdC4gUXVpcyByaXN1ckpXpSMY0j53jg-b-WFChVOmcn5r20RktR66SB3_BYwE=yBzZWQgdnVscHV0YXRlIG9kaW8uIFNhZ2l0dGlzIGFsaXF1YW0gbWFsZXN1YWRhIGJpYmVuZHVt","IGFyY3Ugdml0YWUgZWxlbWRGF3Z0NURns1dDR0MWNfMHJfZHluNG0xYz99VudHVtIGN1cmFiaXR1ci4gSGFiaXRhc3NlIHBsYXRlYSBkaWN0dW1zdCBxdW=","lzcXVlIHNhZ2l0dGlzIHB1cnVzIHNpdCBhbWV0LiBQdXJ1cyBncmF2aWRhIHF1aXMgYmxhbmRpdCB0dXJwaXMgY3Vyc3VzIGluIGhhYyBoYWJpdGFzc2UuIFZvbHV0cGF0IGFjIHRpbmNpZHVudCB2aXRhZSBzZW1wZXIuIFF1YW0gZWxlbWVudHVtIHB1b==","HZpbmFyIGV0aWFtIG5vbiBxdWFtIGxhY3VzLiBBbWV0IHRlbGx1cyBjcmFzIGFkaXBpc2NpbmcgZW5pbSBldSB0dXJwaXMgZWdlc3Rhcy4KCkZldWdpYXQgbmlzbCBwcmV0aXVtIGZ1c2NlIGlkIHZlbGl0IHV0IHRvcnRvciBwcmV0aXVtIHZpdmVycmEuIEVuaW0gZGlhbSB2dWxwdXRhdGUgdXQgcGhhcmV0cmEgc2l0IGFtZ","XQuIEZldWdpYXQgcHJldGl1bSBuaWJoIGlwc3VtIGNvbnNlcXVhdCBuaXNsLiBCaWJlbmR1bSB1dCB0cmlzdGlxdWUgZXQgZWdlc3RhcyBxdWlzIGlwc3VtIHN1c3BlbmRpc3NlIHVsdHJpY2VzLiBWaXZlcnJhIGlwc3VtIG51bmMgYWxpcXVldCBi","aWJlbmR1bSBlbmltIGZhY2lsaXNpcyBncmF2aWRhIG5lcXVlLiBDb25zZWN0ZXR1ciBhZGlwaXNjaW5nIGVsaXQgdXQgYWxpcXVhbSBwdXJ1cyBzaXQgYW1ldCBsdWN0dXMuIEVyYXQgdmVsaXQgc2NlbG","VyaXNxdWUgaW4gZGljdHVtIG5vbiBjb25zZWN0ZXR1ciBhIGVyYXQuIERpYW0gc29sbGljaXR1ZGluIHRlbXBvciBpZCBldSBuaXNsIG51bmMgbWkgaXBzdW0uIFJpc3VzIHF1aXMgdmFyaXVzIHF1YW0gcXVpc3F1ZSBpZCBkaWFtIHZlbCBxdWFtIGV","sZW1lbnR1bS4gUG9zdWVyZSBsb3JlbSBpcHN1bSBkb2xvciBzaXQgYW1ldCBjb25zZWN0ZXR1ci4gVWxsYW1jb3JwZXIgbW9yYmkgdGluY2lkdW50IG9ybmFyZSBtYXNzYS4gUXVhbSBhZGlwaXNjaW5nIHZpdGFlIHByb2luIHNhZ2l0dGlzIG5pc2wgcmhvbmN1cy4gRXUgY29uc2VxdWF0IGFjIGZlbGlzIGRvbmVjIGV0IG9kaW8gcGVsbGVudGVzcX","VlIGRpYW0gdm9sdXRwYXQuIEV0IG1hZ25pcyBkaXMgcGFydHVyaWVudCBtb250ZXMgbmFzY2V0dXIuIEFsaXF1YW0gbWFsZXN1YWRhIGJpYmVuZHVtIGFyY3Ugdml0YWUuIEluIG51bGxhIHBvc3VlcmUgc29sbGljaXR1ZGluIGFsaXF1YW0u"]
blist = ["YzNSbmMyUnlaMlJoWm1kbVJsZEdWMFJFUkVaWFpIZG1Da1pGUmtWSFptUmxaM0puUmtWR1JVZG1aR1ZuY21kemR3cEdSVVpGUjJaa1pXZHlaM04zUmtSRlIwWkhaM05uWkdnS1pXZHlaMFpIVjBaRVJVZEdSMmR6WjJSb1JuTjNSa1JGQ25KblpHVmxSMFpIWjNObmMyVmxSMFpIWjNOblpHaEdjd3BuYzJka2FFVkdSVWRtWkdWbmNrWkdaM05uWkdoeVoyUUtaR1ZuY2taR1ozTm5aR2h5WjJSbFpVZEdSMmRuWkdoeUNtUm9SVVpGUjJaeloyUm9Sbk4zUmtSRlpHZG5kMFpFUlFweVoyUmxaVWRHUjJkelozTmxaVWRHUjJkeloyUm9Sbk1LWjNOblpHaEZSa1ZIWm1SbFozSkdSbWR6WjJSb2NtZGtDbkpuWkdWbFIwWkhaM05uYzJWbFIwWkhaM05uWkdoR2N3cG5jMmRrYUVWR1JVZG1aR1ZuY2taR1ozTm5aR2h5WjJRS1pHVm5ja1pHWjNOblpHaHlaMlJsWlVkR1IyZG5aR2h5Q21Sb1JVWkZSMlp6WjJSb1JuTjNSa1JGWkdkbmQwWkVSUXB5WjJSbFpVZEdSMmR6WjNObFpVZEdSMmR6WjJSb1JuTUtaM05uWkdoRlJrVkhabVJsWjNKR1JtZHpaMlJvY21ka0NtZHpaMlJvY21ka1pXVkhSa2RuYzJka2FFWnpkMFpFUlFweVoyUmxaVWRHUjJkeloyUm9aM05uWkdoR2MzZEdSRVVLY21ka1pXVkhSa2RsWlVkR1IyZHpaMlJvUm5OM1JrUkZDbkpuWkdWbFIwWkhaM05uWkdoRlJrVkhabVJsWjNKR1JncEVZWGRuUTFSR2Uwd3pORkpPWDFRd1gwUXpVRXd3V1gwS2NtZGtaV1ZIUmtkbmMyZGthRVZHUlVkSFJrZG5jMmRrQ25KblpHVmxSMFpIWjNOblpHaEhjMmRrYUVaemQwWkVSUXB5WjJSbFpVZEdSMmR6WjNObFpVZEdSMmR6WjJSb1JuTUtaM05uWkdoRlJrVkhabVJsWjNKR1JtZHpaMlJvY21ka0NtUmxaM0pHUm1keloyUm9jbWRrWldWSFJrZG5aMlJvY2dwa2FFVkdSVWRtYzJka2FFWnpkMFpFUldSblozZEdSRVVLWm1SbFozSkdSbWR6WjJSb2NtZGtaV1ZIUmtkblJVWkZDbVprWldkeVJrWm5jMmRrYUhKblpHVmxhRVp6ZDBaRVJRcHlaMlJsWlVkR1IyZHpaM05sWlVkR1IyZHpaMlJvUm5NS1ozTm5aR2hGUmtWSFptUmxaM0pHUm1keloyUm9jbWRrQ21SbFozSkdSbWR6WjJSb2NtZGtaV1ZIUmtkbloyUm9jZ3BrYUVWR1JVZG1jMmRrYUVaemQwWkVSV1JuWjNkR1JFVUtjbWRrWldWSFJrZG5jMmR6WldWSFJrZG5jMmRrYUVaekNtZHpaMlJvUlVaRlIyWmtaV2R5UmtabmMyZGthSEpuWkFweVoyUmxaVWRHUjJkelozTmxaVWRHUjJkeloyUm9Sbk1LWjNOblpHaEZSa1ZIWm1SbFozSkdSbWR6WjJSb2NtZGtDbVJsWjNKR1JtZHpaMlJvY21ka1pXVkhSa2RuWjJSb2NncGthRVZHUlVkbWMyZGthRVp6ZDBaRVJXUm5aM2RHUkVVS2NtZGtaV1ZIUmtkbmMyZHpaV1ZIUmtkbmMyZGthRVp6Q21keloyUm9SVVpGUjJaa1pXZHlSa1puYzJka2FISm5aQXBrWldkeVJrWm5jMmRrYUhKblpHVmxSMFpIWjJka2FISUtaR2hGUmtWSFpuTm5aR2hHYzNkR1JFVmtaMmQzUmtSRg=="]
@client.event
async def on_message(message):
if message.author == client.user:
return
if message.content.startswith('Yo') or message.content.startswith('yo'):
await message.channel.send(blist[ord(mlist[2][12])-70][ord(klist[1][1])-112:])
client.run('BOT_ID')
The blist has the longest base64 string which got my eyes again. Saved the blist string in base.txt. And Decoded it from base64 multiple times.
mj0ln1r@AHLinux:~/dmbot1$ cat base.txt | base64 -d| base64 -d
gsgdhEFEGfdegrFFgsgdhrgd
rgdeeGFGgsgseeGFGgsgdhFs
gsgdhEFEGfdegrFFgsgdhrgd
degrFFgsgdhrgdeeGFGggdhr
dhEFEGfsgdhFswFDEdggwFDE
rgdeeGFGgsgseeGFGgsgdhFs
gsgdhEFEGfdegrFFgsgdhrgd
gsgdhrgdeeGFGgsgdhFswFDE
rgdeeGFGgsgdhgsgdhFswFDE
rgdeeGFGeeGFGgsgdhFswFDE
rgdeeGFGgsgdhEFEGfdegrFF
DawgCTF{L34RN_T0_D3PL0Y}
rgdeeGFGgsgdhEFEGGFGgsgd
rgdeeGFGgsgdhGsgdhFswFDE
rgdeeGFGgsgseeGFGgsgdhFs
gsgdhEFEGfdegrFFgsgdhrgd
degrFFgsgdhrgdeeGFGggdhr
dhEFEGfsgdhFswFDEdggwFDE
fdegrFFgsgdhrgdeeGFGgEFE
Flag : DawgCTF{L34RN_T0_D3PL0Y}
DM Bot?
Attached File : bot.py
bot.py
#BY: J4NU5
import discord
STRING = 4
START = 22
STOP = 58
if __name__ == "__main__":
client = discord.Client(intents=discord.Intents.default())
@client.event
async def on_ready():
print('We have logged in as {0.user}'.format(client))
msglist = ["TG9yZW0gaXBzdW0gZG9sb3Igc2l0IGFtZXQsIGNvbnNlY3RldHVyIGFkaX","Bpc2NpbmcgZWxpdCwgc2VkIGRvIGVpdXNtb2QgdGVtcG9yIGluY2lkaWR1bnQgdXQgbGFib3JlIGV0IGRvbG9yZSBtYWduYSBhbGlxdWEuIFVybmEgY29uZGltZW50dW0gbWF0dGlzIHBlbGxlbnRlc3F1ZSBpZCBuaWJoIHRvcnRvciBpZCBhbGlxdWV0LiBGYW==","NpbGlzaXMgbWFnbmEgZXRpYW0gdGVtcG9yIG9yY2kgZXUuIFNhcGllbiBldCBsaWd1bGEgdWxsYW1jb3JwZXIgbWFsZXN1YWRhLiBUcmlzdGlxdWUgbnVsbGE","gYWxpcXVldCBlbmltIHRvcnRvciBhdC4gUXVpcyByaXN1cyBzZWQgdnVscHV0YXRlIG9kaW8uIFNhZ2l0dGlzIGFsaXF1YW0gbWFsZXN1YWRhIGJpYmVuZHVt","IGFyY3Ugdml0YWUgZWxlbWRGF3Z0NURns1dDR0MWNfMHJfZHluNG0xYz99VudHVtIGN1cmFiaXR1ci4gSGFiaXRhc3NlIHBsYXRlYSBkaWN0dW1zdCBxdW=","lzcXVlIHNhZ2l0dGlzIHB1cnVzIHNpdCBhbWV0LiBQdXJ1cyBncmF2aWRhIHF1aXMgYmxhbmRpdCB0dXJwaXMgY3Vyc3VzIGluIGhhYyBoYWJpdGFzc2UuIFZvbHV0cGF0IGFjIHRpbmNpZHVudCB2aXRhZSBzZW1wZXIuIFF1YW0gZWxlbWVudHVtIHB1b==","HZpbmFyIGV0aWFtIG5vbiBxdWFtIGxhY3VzLiBBbWV0IHRlbGx1cyBjcmFzIGFkaXBpc2NpbmcgZW5pbSBldSB0dXJwaXMgZWdlc3Rhcy4KCkZldWdpYXQgbmlzbCBwcmV0aXVtIGZ1c2NlIGlkIHZlbGl0IHV0IHRvcnRvciBwcmV0aXVtIHZpdmVycmEuIEVuaW0gZGlhbSB2dWxwdXRhdGUgdXQgcGhhcmV0cmEgc2l0IGFtZ","XQuIEZldWdpYXQgcHJldGl1bSBuaWJoIGlwc3VtIGNvbnNlcXVhdCBuaXNsLiBCaWJlbmR1bSB1dCB0cmlzdGlxdWUgZXQgZWdlc3RhcyBxdWlzIGlwc3VtIHN1c3BlbmRpc3NlIHVsdHJpY2VzLiBWaXZlcnJhIGlwc3VtIG51bmMgYWxpcXVldCBi","aWJlbmR1bSBlbmltIGZhY2lsaXNpcyBncmF2aWRhIG5lcXVlLiBDb25zZWN0ZXR1ciBhZGlwaXNjaW5nIGVsaXQgdXQgYWxpcXVhbSBwdXJ1cyBzaXQgYW1ldCBsdWN0dXMuIEVyYXQgdmVsaXQgc2NlbG","VyaXNxdWUgaW4gZGljdHVtIG5vbiBjb25zZWN0ZXR1ciBhIGVyYXQuIERpYW0gc29sbGljaXR1ZGluIHRlbXBvciBpZCBldSBuaXNsIG51bmMgbWkgaXBzdW0uIFJpc3VzIHF1aXMgdmFyaXVzIHF1YW0gcXVpc3F1ZSBpZCBkaWFtIHZlbCBxdWFtIGV","sZW1lbnR1bS4gUG9zdWVyZSBsb3JlbSBpcHN1bSBkb2xvciBzaXQgYW1ldCBjb25zZWN0ZXR1ci4gVWxsYW1jb3JwZXIgbW9yYmkgdGluY2lkdW50IG9ybmFyZSBtYXNzYS4gUXVhbSBhZGlwaXNjaW5nIHZpdGFlIHByb2luIHNhZ2l0dGlzIG5pc2wgcmhvbmN1cy4gRXUgY29uc2VxdWF0IGFjIGZlbGlzIGRvbmVjIGV0IG9kaW8gcGVsbGVudGVzcX","VlIGRpYW0gdm9sdXRwYXQuIEV0IG1hZ25pcyBkaXMgcGFydHVyaWVudCBtb250ZXMgbmFzY2V0dXIuIEFsaXF1YW0gbWFsZXN1YWRhIGJpYmVuZHVtIGFyY3Ugdml0YWUuIEluIG51bGxhIHBvc3VlcmUgc29sbGljaXR1ZGluIGFsaXF1YW0u"]
@client.event
async def on_message(message):
if message.author == client.user:
return
if message.content.startswith('hello') or message.content.startswith('Hello') or message.content.startswith('hi') or message.content.startswith('Hi'):
await message.channel.send(msglist[STRING][START:STOP])
client.run('THIS_SHOULD_PROBABLY_BE_A_PROPER_BOT_ID')
Again some base64 encodes! This time observed the program. The message which is sending to the user is message.channel.send(msglist[STRING][START:STOP])
The msglist is the list given, STRING = 4 START = 22 STOP = 58. So I tried to decode the string from 22 to 58th character of 4th index string list. This solve.py will print the flag.
import base64
#msglist[4][22:58]
msg = "IGFyY3Ugdml0YWUgZWxlbWRGF3Z0NURns1dDR0MWNfMHJfZHluNG0xYz99VudHVtIGN1cmFiaXR1ci4gSGFiaXRhc3NlIHBsYXRlYSBkaWN0dW1zdCBxdW"
msg = msg[22:58]
decoded_string = base64.b64decode(msg)
print(decoded_string)
# DawgCTF{5t4t1c_0r_dyn4m1c?}
Flag : DawgCTF{5t4t1c_0r_dyn4m1c?}
Binary Bomb Phase 1
Attached File : dawg_bbomb
I used the ltrace to execute this binary file.
mj0ln1r@AHLinux:~/Desktop/CYBER/CTF/CTFTime/17_DawgCTF/binary_bomb/phase-2$ ltrace ./dawg_bbomb
sysconf(30, 0x7fff11d7a628, 0x7fff11d7a638, 0x5593c3601dc0) = 4096
mprotect(0x5593c35fb000, 389, 7, 389) = 0
getppid() = 27043
snprintf("/proc/27043/status", 24, "/proc/%d/status", 27043) = 18
fopen("/proc/27043/status", "r") = 0x5593c3c032a0
fgets("Name:\tltrace\n", 16, 0x5593c3c032a0) = 0x7fff11d7a580
fclose(0x5593c3c032a0) = 0
strstr("Name:\tltrace\n", "gdb") = nil
strstr("Name:\tltrace\n", "ltrace") = "ltrace\n"
time(0) = 1682156350
srand(0x6443ab3e, 0x5593c35fe022, 0, 0) = 1
rand(0xffffffff, 0x7f41b6e19860, 0x7f41b6e19204, 0x7f41b6e19280) = 0x3ee147ca
time(0) = 1682156350
srand(0x6443ab3e, 0x7fff11d7a628, 0, 0x5593c3601dc8) = 1
setlocale(LC_ALL, "") = "en_IN"
sigaction(SIGINT, { 0x5593c35fd707, <>, 0, 0 }, nil) = 0
puts("Welcome to the DawgCTF Binary Bo"...Welcome to the DawgCTF Binary Bomb!
) = 36
printf("Type HELP for help.") = 19
printf("\033[33m\ns\n\033[0m", "Starting off with small strings."...Type HELP for help.
Starting off with small strings...
) = 45
printf("Enter round %d input: ", 1) = 21
getline(0x7fff11d7a3f8, 0x7fff11d7a400, 0x7f41b6e19aa0, 0x7fff11d7a400Enter round 1 input: pass
) = 5
realloc(0, 5) = 0x5593c3c04e70
strncpy(0x5593c3c04e70, "pass", 5) = 0x5593c3c04e70
strncmp("pass", "SKIP", 4) = 29
strncmp("pass", "HELP", 4) = 40
strncmp("pass", "BabYs_F1rS7_RE", 4) = 46
rand(1, 0x5593c35fe1dc, 0, 66) = 0x3ee147ca
calloc(160, 1) = 0x5593c3c04e90
sprintf("Round 1 EXPLODED!", "Round %d EXPLODED!", 1) = 17
printf("\033[31m%s\n\033[0m", "Round 1 EXPLODED!"Round 1 EXPLODED!
) = 27
free(0x5593c3c04e90) = <void>
printf("\033[33m\n%s\n\033[0m", "Starting off with small strings."...
Starting off with small strings...
) = 45
printf("Enter round %d input: ", 1) = 21
getline(0x7fff11d7a3f8, 0x7fff11d7a400, 0x7f41b6e19aa0, 0x7fff11d7a400Enter round 1 input: BabYs_F1rS7_RE
) = 15
realloc(0x5593c3c04e70, 15) = 0x5593c3c04e70
strncpy(0x5593c3c04e70, "BabYs_F1rS7_RE", 15) = 0x5593c3c04e70
strncmp("BabYs_F1rS7_RE", "SKIP", 14) = -17
strncmp("BabYs_F1rS7_RE", "HELP", 14) = -6
strncmp("BabYs_F1rS7_RE", "BabYs_F1rS7_RE", 14) = 0
strlen("BabYs_F1rS7_RE") = 14
rand(1, 0x5593c35fe1dc, 0x4000, 476) = 0x578116f8
calloc(100, 1) = 0x5593c3c04f40
sprintf("Defused phase 1", "Defused phase %d", 1) = 15
printf("\033[32m%s\n\033[0m", "Defused phase 1"Defused phase 1
) = 25
free(0x5593c3c04f40) = <void>
printf("\033[35mFlag: DawgCTF{s}\n\033[0m", "BabYs_F1rS7_RE"Flag: DawgCTF{BabYs_F1rS7_RE}
) = 39
printf("\033[33m\n%s\n\033[0m", "Can you help me? I lost my key a"...
Can you help me? I lost my key and can't read my string
) = 66
printf("Enter round %d input: ", 2) = 21
getline(0x7fff11d7a3f8, 0x7fff11d7a400, 0x7f41b6e19aa0, 0x7fff11d7a400Enter round 2 input:
printf("Enter round %d input: ", 1) For this I entered a test value pass Then I observer in ltrace that it is compared with BabYs_F1rS7_RE If the input matched with BabYs_F1rS7_RE The program is going to print the flag for us. So I inputted the BabYs_F1rS7_RE and got the flag.
Flag : DawgCTF{BabYs_F1rS7_RE}
Binary Bomb Phase 2
Attached File : dawg bbomb
I used the ltrace to execute this binary file again and It prompted for the first round input I already solved it so by giving it to the program we can move to next phase or we can use SKIP to move to the next phase.
mj0ln1r@AHLinux:~/Desktop/CYBER/CTF/CTFTime/17_DawgCTF/binary_bomb/phase-2$ ltrace ./dawg_bbomb
Enter round 2 input: pass
) = 5
realloc(0x559057ff4e70, 5) = 0x559057ff4e70
strncpy(0x559057ff4e70, "pass", 5) = 0x559057ff4e70
strncmp("pass", "SKIP", 4) = 29
strncmp("pass", "HELP", 4) = 40
strncmp("yhzz", "]a=gbVPf\\VO9{VA:ey8gn", 4) = 28
rand(2, 0x559057ce01eb, 0, 93) = 0x280e2a51
calloc(160, 1) = 0x559057ff4e90
Again I passed the test value pass to the round 2 input. This time the pass is converted as yhzz and compared with a=gbVPf\\VO9{VA:ey8gn I copied this string and inputed this value to the round 2 program.
mj0ln1r@AHLinux:~/Desktop/CYBER/CTF/CTFTime/17_DawgCTF/binary_bomb/phase-2$ ltrace ./dawg_bbomb
Enter round 2 input: ]a=gbVPf\\VO9{VA:ey8gn
) = 23
realloc(0x559057ff4e70, 23) = 0x559057ff4e70
strncpy(0x559057ff4e70, "]a=gbVPf\\\\VO9{VA:ey8gn", 23) = 0x559057ff4e70
strncmp("]a=gbVPf\\\\VO9{VA:ey8gn", "SKIP", 22) = 10
strncmp("]a=gbVPf\\\\VO9{VA:ey8gn", "HELP", 22) = 21
strncmp("Th4nk_YoUU_F0r_H3lp1ng", "]a=gbVPf\\VO9{VA:ey8gn", 22) = -9
rand(2, 0x559057ce01eb, 0, 93) = 0x39aba478
calloc(160, 1)
So, this time the ]a=gbVPf\\\\VO9{VA:ey8gn is conveted Th4nk_YoUU_F0r_H3lp1ng. That means if we give Th4nk_YoUU_F0r_H3lp1ng to the round 2 we this be converted to ]a=gbVPf\\\\VO9{VA:ey8gn and will be compared with ]a=gbVPf\\VO9{VA:ey8gn.
Closely observe that ]a=gbVPf\\\\VO9{VA:ey8gn != ]a=gbVPf\\VO9{VA:ey8gn , Because of the extra \\ These two extra slashes are generated by on extra U in the Th4nk_YoUU_F0r_H3lp1ng , So I removed the extra U and submitted to the round 2 input ultimately the comparision will be successfull, the program will print the flag
mj0ln1r@AHLinux:~/Desktop/CYBER/CTF/CTFTime/17_DawgCTF/binary_bomb/phase-2$ ltrace ./dawg_bbomb
Enter round 2 input: Th4nk_YoU_F0r_H3lp1ng
) = 22
realloc(0x559057ff5150, 22) = 0x559057ff5150
strncpy(0x559057ff5150, "Th4nk_YoU_F0r_H3lp1ng", 22) = 0x559057ff5150
strncmp("Th4nk_YoU_F0r_H3lp1ng", "SKIP", 21) = 1
strncmp("Th4nk_YoU_F0r_H3lp1ng", "HELP", 21) = 12
strncmp("]a=gbVPf\\VO9{VA:ey8gn", "]a=gbVPf\\VO9{VA:ey8gn", 21) = 0
strlen("]a=gbVPf\\VO9{VA:ey8gn") = 21
rand(2, 0x559057ce01f0, 0x1fe00000, 11) = 0x40d2c90b
calloc(100, 1) = 0x559057ff5390
sprintf("You did it!!", "You did it!!") = 12
printf("\033[32m%s\n\033[0m", "You did it!!"You did it!!
) = 22
free(0x559057ff5390) = <void>
printf("\033[35mFlag: DawgCTF{s}\n\033[0m", "Th4nk_YoU_F0r_H3lp1ng"Flag: DawgCTF{Th4nk_YoU_F0r_H3lp1ng}
) = 46
Flag : DawgCTF{Th4nk_YoU_F0r_H3lp1ng}
Binary Bomb Phase 3
Attached File : dawg_bbomb
This is most frustated challenge I solved in CTF.
I used the ltrace to execute this binary file again and It prompted for the first two rounds input I already solved them so by giving the answers to the program we can move to next phase or we can use SKIP to move to the next phase.
mj0ln1r@AHLinux:~/Desktop/CYBER/CTF/CTFTime/17_DawgCTF/binary_bomb/phase-2$ ltrace ./dawg_bbomb
printf("\033[33m\n%s\n\033[0m", "I've been spun around so much..."...
I've been spun around so much... my head kinda hurts now :/
) = 70
printf("Enter round %d input: ", 3) = 21
getline(0x7ffc8245d518, 0x7ffc8245d520, 0x7f0568419aa0, 0x7ffc8245d520Enter round 3 input: pass
) = 5
realloc(0x559057ff5150, 5) = 0x559057ff5150
strncpy(0x559057ff5150, "pass", 5) = 0x559057ff5150
strncmp("pass", "SKIP", 4) = 29
strncmp("pass", "HELP", 4) = 40
strncmp("iZll", "siDgabDzXZa]XsibaabgMXGa]XlpDgaO"..., 4) = -10
rand(3, 0x559057ce0208, 0, 115) = 0x69bce1ad
calloc(160, 1) = 0x559057ff5400
sprintf("So close, but yet, so far...", "So close, but yet, so far...") = 28
As the text of the phase 3 says it is spun around. So I think the input we given is roted by some value and then compared with siDgabDzXZa]XsibaabgMXGa]XlpDgaO.
The test value pass is converted to iZll the rotated amount is 87
When I use test as input it got converted as mxml but this isn't any known rotation. So we cant simply use rot87.
My aim is to get the string which can be converted to siDgabDzXZa]XsibaabgMXGa]XlpDgaO. So , I started finding each letter manually(frustrated).
I found that S is converted to s and noted the [ rotation amount is 32 ]
p is converted to i [ rotation amount is 87]
1 is converted to D [ rotation amount is 19 ]
n is converted to g [ rotation amount is 87 ]
The string recovered Sp1n is going to be converted to siDg, and still I have to recover the abDzXZa]XsibaabgMXGa]XlpDgaO
But there is a point to catch, The rotation is done randomly with the amount [87 or 19 or 32]
So, I took the encoded string abDzXZa]XsibaabgMXGa]XlpDgaO and started rotating each and every character with these three amounts, I noted the recovered string if it has any pattern in it.
By doing this process for an half and hour, I found this strings Sp1nNi1g_aNd_SpiNNinG_4Nd_sP1nNI This is the string which can be converted to siDgabDzXZa]XsibaabgMXGa]XlpDgaO.
I thought that this was the right answer to the phase 3, but not.
mj0ln1r@AHLinux:~/Desktop/CYBER/CTF/CTFTime/17_DawgCTF/binary_bomb/phase-2$ ltrace ./dawg_bbomb
Enter round 3 input: Sp1nNi1g_aNd_SpiNNinG_4Nd_sP1nNI
) = 33
realloc(0x559057ff5150, 33) = 0x559057ff5150
strncpy(0x559057ff5150, "Sp1nNi1g_aNd_SpiNNinG_4Nd_sP1nNI"..., 33) = 0x559057ff5150
strncmp("Sp1nNi1g_aNd_SpiNNinG_4Nd_sP1nNI"..., "SKIP", 32) = 37
strncmp("Sp1nNi1g_aNd_SpiNNinG_4Nd_sP1nNI"..., "HELP", 32) = 11
strncmp("siDgabDzXZa]XsibaabgMXGa]XlpDgaO"..., "siDgabDzXZa]XsibaabgMXGa]XlpDgaO"..., 32) = 0
strlen("siDgabDzXZa]XsibaabgMXGa]XlpDgaO"...) = 34
rand(3, 0x559057ce0210, 0x800400000000, 8) = 0xee19b98
calloc(160, 1) = 0x559057ff5400
sprintf("Better luck on phase 4", "Better luck on phase %d", 4) = 22
The comparision is done as the strncmp resulted 0 but this didn't give me any flag. So, after a while I tried to make it meaningfull to read
I changed Sp1nNi1g_aNd_SpiNNinG_4Nd_sP1nNI to Sp1nNi1g_aNd_SpiNNinG_4Nd_sP1nNIng added ng at the end.
mj0ln1r@AHLinux:~/Desktop/CYBER/CTF/CTFTime/17_DawgCTF/binary_bomb/phase-2$ ltrace ./dawg_bbomb
Enter round 3 input: Sp1nNi1g_aNd_SpiNNinG_4Nd_sP1nNIng
) = 35
realloc(0x559057ff5150, 35) = 0x559057ff5150
strncpy(0x559057ff5150, "Sp1nNi1g_aNd_SpiNNinG_4Nd_sP1nNI"..., 35) = 0x559057ff5150
strncmp("Sp1nNi1g_aNd_SpiNNinG_4Nd_sP1nNI"..., "SKIP", 34) = 37
strncmp("Sp1nNi1g_aNd_SpiNNinG_4Nd_sP1nNI"..., "HELP", 34) = 11
strncmp("siDgabDzXZa]XsibaabgMXGa]XlpDgaO"..., "siDgabDzXZa]XsibaabgMXGa]XlpDgaO"..., 34) = 0
strlen("siDgabDzXZa]XsibaabgMXGa]XlpDgaO"...) = 34
rand(3, 0x559057ce0210, 0x800400000000, 8) = 0x48a902d4
calloc(100, 1) = 0x559057ff5400
sprintf("Phase 3 locked down", "Phase %d locked down", 3) = 19
printf("\033[32m%s\n\033[0m", "Phase 3 locked down"Phase 3 locked down
) = 29
free(0x559057ff5400) = <void>
printf("\033[35mFlag: DawgCTF{s}\n\033[0m", "Sp1nNi1g_aNd_SpiNNinG_4Nd_sP1nNI"...Flag: DawgCTF{Sp1nNi1g_aNd_SpiNNinG_4Nd_sP1nNIng}
) = 59
And finally, This gave me the flag.[A long deep breath]
Flag : DawgCTF{Sp1nNi1g_aNd_SpiNNinG_4Nd_sP1nNIng}
And thats a wrap, Thank You for Reading..!